Rule
ID |
Rule Identifier |
Rule Version |
Repu- tation |
Name |
Description |
Long Description |
| 0 |
0 |
0 |
-1 |
Not Applicable |
No rule affects this reputation. |
No rule affects this reputation. |
| 1 |
589825 |
9 |
-1 |
Use certificate reputation to identify trusted or malicious files |
Determines if a file is trusted or malicious based on the GTI or Enterprise reputation of the signing certificate. |
This rule determines if a file is trusted or malicious based on the GTI or Enterprise reputation of the signing certificate. The certificate reputation must be Known Malicious, Known Trusted, Most Likely Malicious, or Most Likely Trusted. |
| 2 |
196610 |
3 |
-1 |
Use Enterprise file reputation to identify trusted or malicious files |
Determines if a file is trusted or malicious based on the file's Enterprise reputation. |
This rule determines if a file is trusted or malicious based on the file's Enterprise reputation. The reputation must be at least Known Malicious, Known Trusted, Most Likely Malicious, or Most Likely Trusted. |
| 3 |
65539 |
1 |
0 |
Bypass Lookup for files based on selection criteria |
Bypass GTI lookup for files based on selection criteria that are likely to be clean or unknown to GTI. |
Bypass GTI lookup for files based on selection criteria that are likely to be clean or unknown to GTI. |
| 4 |
196612 |
3 |
-1 |
Use GTI file reputation to identify trusted or malicious files |
Determines if a file is trusted or malicious based on the file's GTI reputation. |
This rule determines if a file is trusted or malicious based on the file's GTI reputation. The reputation must be at least Known Malicious, Known Trusted, Most Likely Malicious, or Most Likely Trusted. |
| 5 |
327685 |
5 |
-1 |
Use GTI URL reputation to identify trusted or malicious processes |
Mitre-T1204. Determines if a process is trusted or malicious based on the GTI URL reputation. |
Tactic: Execution - Technique: T1204. This rule determines if a process is trusted or malicious based on the GTI URL reputation. |
| 10 |
262154 |
4 |
100 |
Identify that a file is the main component of a trusted installer using the file's attributes, certificate reputation, and file reputation. |
Determines whether a file is a trusted installer based on the file's attributes, file name, and the GTI or Enterprise certificate and file reputation. |
This rule determines if file is a trusted installer based on the file's GTI or Enterprise reputation. It also looks at the file name, company name, and other similar attributes to determine if it's an updater or installer component that can be trusted. |
| 12 |
131084 |
2 |
100 |
Identify that a file is the main component of a trusted installer based on a specific file identified by hash |
Determines whether a file is a trusted installer based on the file hash and the GTI or Enterprise reputation. |
This rule determines if the file is a trusted installer based on the file's hash and GTI or Enterprise file reputation to determine if it's an updater or installer component that can be trusted. |
| 20 |
131092 |
2 |
-1 |
Identify trusted files with McAfee Privileges |
Identifies trusted files using certificates or hashes that are distributed in the AV DAT files. |
This rule identifies trusted files using certificates or hashes that are distributed in the AV DAT files and can also have elevated privileges with McAfee processes and drivers. |
| 34 |
131106 |
2 |
1 |
SFv3 Verification |
Identifies a test sample that can be used for SFv3 validation |
This rule identifies a test sample by hash that can be used for verification of the SFv3 framework. |
| 35 |
196643 |
3 |
1 |
Installation Verification |
Identifies a test sample that can be used for installation verification. |
This rule identifies a test sample that can be used for installation verification. |
| 36 |
65572 |
1 |
1 |
Installation Verification with no TIE Server |
Identifies a test sample that can be used for installation verification in a configuration with no TIE Server. |
This rule identifies a test sample that can be used for installation verification in a configuration with no TIE Server. |
| 38 |
131110 |
2 |
1 |
SFv3 Verification Rule disabled in cloud |
A test rule that is disabled in cloud for SFv3 validation |
This rule identifies a test sample by hash and is disabled in cloud for verification of the SFv3 framework. |
| 50 |
65586 |
1 |
85 |
Identify trusted files from a trusted creator |
Identifies trusted files that were created by a fully trusted updater. |
This rule identifies trusted files that were created by a fully trusted updater and haven't been modified. |
| 51 |
131123 |
2 |
-1 |
Identify files marked as trusted installers by the Trust Scanner |
Identifies files that are marked as trusted by the Trust scanner which is based off the dat file. |
This rule identifies files that are marked as trusted installer files by Trust scanner based on the information available in the dat file and isn't cloud dependent. |
| 55 |
131127 |
2 |
99 |
Identify certificates needing reputation correction |
Identifies certificates from Tier1 vendors that need a correction to their reputation level. |
This rule identifies certificates from Tier1 vendors that need a correction to their reputation level. |
| 57 |
262201 |
4 |
-1 |
Use GTI file reputation to identify files that Might be Trusted or Might be Malicious |
Determines files which Might be Trusted or Might be Malicious based on GTI file reputation. |
This rule identifies files which are less conclusive in their GTI reputation such as Might be Trusted and Might be Malicious. |
| 58 |
196878 |
3 |
70 |
Identify trust for files executed on network shares |
This rule identifies trust for files executed on network shares using file attributes and other related information like prevalence. |
This rule identifies trust for files executed on network shares using scanner results and file attributes to indicate trust. |
| 60 |
131132 |
2 |
0 |
Attribute setting rule to aid in identifying interesting files |
Identifies items launched by an interesting actor or is an internet facing item. |
Identifies files that are launched by an interesting actor or has special characteristics such as self-signed cert. |
| 61 |
262205 |
4 |
0 |
Identify internet facing applications |
Identify popular internet facing applications such as a web browser or email client. |
This rule identifies internet facing applications such as a web browser or email client by using identifiable attributes such as file name and certificate. |
| 62 |
196670 |
3 |
0 |
Identify an application which reads content files |
Identifies an application that reads content files such as PDF documents, Microsoft Office documents, and videos. |
This rule identifies the main executable file of popular applications which read content such as PDF documents, Microsoft Office documents, and videos. |
| 95 |
131167 |
2 |
85 |
Identify files that are signed by certificate of known clean reputation and mark them Most Likely Trusted when offline |
Identifies files that are signed by certificate of known clean reputation and mark them Most Likely Trusted when offline. |
Identifies files that are signed by certificate of known clean reputation and mark them Most Likely Trusted when in No connectivity mode. |
| 96 |
65632 |
1 |
0 |
Intelligent Prompt |
Suppress prompting for library loads for trusted applications other than Internet browsers. |
This rule suppresses prompting for library loads for trusted applications other than Internet browsers. |
| 97 |
262241 |
4 |
70 |
Trust files while offline unless highly suspicious for JTI Scanner versions released after June 2018 |
Determines that files with no suspicious characteristics are trusted when the system is offline (disconnected from TIE and GTI). |
This rule treats files that have no suspicious characteristics as trusted when the system is disconnected from the TIE server and from GTI. This rule uses less rigorous criteria for determining trust to help mitigate issues with large numbers of Unknown files while disconnected from the TIE Server or GTI. This Rule applies to JTI Scanner version 2.1.4.1590 and above, released June 2018. |
| 98 |
262242 |
4 |
70 |
Trust files while offline unless highly suspicious for JTI Scanner versions released prior to June 2018. |
Determines that files with no suspicious characteristics are trusted when the system is offline (disconnected from TIE and GTI). |
This rule treats files that have no suspicious characteristics as trusted when the system is disconnected from the TIE server and from GTI. This rule uses less rigorous criteria for determining trust to help mitigate issues with large numbers of Unknown files while disconnected from the TIE Server or GTI. This Rule applies to JTI Scanner versions below 2.1.4.1590, released June 2018. |
| 99 |
196707 |
3 |
50 |
Trust files based on Low Change Systems security level when offline |
Determines that files with no suspicious characteristics are unknown when the system is offline (disconnected from the TIE server and from GTI). |
Treats files with no suspicious characteristics as unknown when the system is disconnected from the TIE server and from GTI. This is the last rule to execute. |
| 125 |
262269 |
4 |
85 |
Identify files marked as Trusted Windows AppStore Applications |
Identifies files that are marked as trusted Windows AppStore Applications, which are based off the file and process attributes. |
This rule identifies files that are marked as trusted Windows AppStore Applications based on the file attributes, file location, and process attributes. |
| 126 |
393342 |
6 |
85 |
Identify trusted signed applications |
Identifies files that are signed and located in paths commonly used for installing programs. They also can have a Start menu entry. |
This rule identifies files that are signed and have a valid non self-signed certificate. File location is considered along with environmental attributes such as Start menu entry. |
| 127 |
196735 |
3 |
85 |
Identify trusted Help resource libraries |
Identifies signed resource libraries that are used by trusted software. |
This rule identifies resource libraries that are used by trusted software. The files are signed and don't have a malicious certificate reputation. They have characteristics indicating it's a resource library, such as no imports or exports and a few Portable Executable (PE) Sections. |
| 128 |
196736 |
3 |
85 |
Identify trusted help resource libraries |
Identifies signed resource libraries that are used by trusted software. These libraries are generally used as part of Help documentation. |
This rule identifies signed resource libraries that are used by trusted software. The libraries are generally used as part of the application Help documentation. They're signed and don't have a malicious certificate reputation. They have characteristics indicating it's a resource library such as no imports or exports and a few Portable Executable (PE) Sections. They're also located in application installation folders. |
| 129 |
262273 |
4 |
85 |
Identify trusted signed utility applications |
Identifies utility applications that are signed and the certificate isn't distrusted. These files don't launch on startup and have characteristics that suggest they're utility programs. |
This rule identifies utility applications that are signed and the certificate isn't distrusted. These files don't launch on startup. They're located in a folder which is indicative of a tool or installed program (example: %programfiles%\subfolder) and import APIs and have other characteristics that are consistent with trusted utility applications. |
| 130 |
327810 |
5 |
85 |
Identify trusted signed drivers |
Identifies device drivers that are signed and installed on the local system. |
This rule identifies device drivers that are signed and installed on the local system. They use the native subsystem and are located in the %windir%\system32\drivers or driverstore folders. |
| 131 |
327811 |
5 |
85 |
Identify trusted signed Digital Rights Management (DRM) libraries |
Identifies signed trusted Digital Rights Management libraries used by Windows. |
This rule identifies trusted Digital Rights Management libraries that are signed and whose certificate is trusted. These files are in the Windows DRM and DRM cache folders. |
| 132 |
262276 |
4 |
85 |
Identify trusted signed files |
Identifies files that are signed and trusted, and whose certificate reputation is trusted. |
This rule identifies files that are signed and trusted, and whose certificate is also trusted. |
| 133 |
262277 |
4 |
70 |
Identify trusted files on the disk |
Identifies files that are present on the disk and aren't suspicious before installing the TIE module. |
This rule identifies files that are on the disk and aren't suspicious before installing the TIE module. They haven't been tampered with as identified by the NTFS file journaling. |
| 134 |
327814 |
5 |
85 |
Identify trusted files on the disk that were prevalent in the enterprise prior to installing the TIE module. |
Identifies files that are present on the disk and aren't suspicious before installing the TIE module and have been seen in the enterprise. |
This rule identifies files that are on the disk and aren't suspicious before installing the TIE module. They haven't been tampered with as identified by the NTFS file journaling. The files must also have been seen in the enterprise. |
| 136 |
327816 |
5 |
85 |
Identify unsigned NativeImage Files that Might Be Trusted |
Detects NativeImage Files that aren't signed with a known trusted certificate. These files are often low prevalence and may be unique to a system. |
This rule detects precompiled binary files that Might Be Trusted that have been installed into the NativeImages folder and don't contain suspicious attributes. |
| 137 |
196745 |
3 |
85 |
Identify unsigned DOTNet assemblies that Might Be Trusted |
Detects DOTNet assemblies that aren't signed with a known trusted certificate. These files are often low prevalence and may be unique to a system. |
This rule detects files that Might Be Trusted that have been installed into the global assembly cache folders and don't contain suspicious attributes. These files are often on few systems in the network and may include pre-compiled DOTNet native image files and similar assemblies. |
| 138 |
393354 |
6 |
85 |
Identify trusted unsigned Microsoft DOTNet assemblies |
Detects Microsoft DOTNet assemblies that aren't signed with a known trusted certificate. These files may not be present on many machines within the enterprise. |
This rule detects Microsoft-provided files that have CLR code (DOTNet), have been installed into the global assembly cache folders, and don't contain suspicious attributes. The files may or may not be found on multiple machines within the enterprise, which could include just-in-time compiled assemblies. |
| 139 |
327819 |
5 |
85 |
Identify trusted DOTNet assemblies |
Detects DOTNet assemblies that have been installed into the global assembly cache and are present on multiple machines. |
This rule detects files that have CLR code (DOTNet) and have been installed into the global assembly cache folders. The files are present on multiple machines within the enterprise, indicating they aren't just-in-time compiled assemblies. |
| 140 |
196748 |
3 |
85 |
Identify trusted prevalent files |
Detects files that have been present in the enterprise for a long time and are prevalent across multiple machines. |
This rule detects files that are trusted because they're widespread and well known. The files are present on multiple machines within the enterprise and have been known for more than 3 months. |
| 151 |
196759 |
3 |
70 |
Identify web installers |
Identifies web installers that are signed and whose certificate isn't distrusted. It also identifies the company, product, and version. |
This rule identifies web installers that are signed and whose certificate isn't distrusted. It also identifies the web installer's company, product, and version. |
| 152 |
327832 |
5 |
70 |
Identify safe files extracted by Windows Installer |
Identifies safe files extracted by Windows Installer installer based on the actor process, certificate, and cloud reputation. |
This rule identifies safe files extracted by Windows Installer based on actor process, certificate, and cloud reputation. If anything is suspicious about the installer dropped file, the rule doesn't yield a clean reputation. |
| 153 |
131225 |
2 |
70 |
Identify files that ATD doesn't report as suspicious |
Identifies files that Advanced Threat Defense doesn't report as suspicious. |
This rule identifies files that have been assessed by Advanced Threat Defense and aren't reported as suspicious. |
| 205 |
262349 |
4 |
30 |
Identify suspicious files that have odd creation dates and are likely not packed |
Identifies suspicious files that are likely not packed, have odd creation dates, and are in locations such as the Temp or Downloads folders. |
This rule identifies suspicious files in locations such as the Temp or Downloads folders. These files are likely not packed and there's evidence that the date properties have been tampered. |
| 206 |
65742 |
1 |
30 |
Identify suspicious files that have odd creation dates and are likely packed |
Identifies suspicious files anywhere on the system. The files are likely packed and show evidence that the date has been tampered. |
This rule identifies suspicious files located anywhere on the system. These files are identified as packed and there's evidence that the date properties have been tampered. |
| 207 |
196815 |
3 |
15 |
Identify suspicious files executing from the Recycle bin |
Identifies suspicious files that are executed from the Recycle bin. |
This rule identifies suspicious files that reside in and are executed from the Recycle bin. |
| 208 |
65744 |
1 |
15 |
Identify suspicious files executing from the roaming folder |
Identifies suspicious files that are executed or loaded from the user's roaming folder. |
This rule identifies suspicious files that are executed or loaded from the user's roaming folder (%userprofile%\appdata\roaming) in an incorrect way. |
| 209 |
196817 |
3 |
15 |
Identify suspicious files that are hidden from the user |
Identifies suspicious files that are executed or loaded while hidden from the user. |
This rule identifies suspicious files that are executed or loaded, and are hidden from the using a mechanism such as a file attribute. These files appear to be critical operating system files but aren't. |
| 211 |
65747 |
1 |
15 |
Identify suspicious files created by an untrusted process |
Identifies suspicious files created with a process that has a suspicious or known malicious reputation. |
This rule identifies a file that is suspicious because the process that created it has a reputation of Might be Malicious to Known Malicious at the time of creation. The file also hasn't been modified since its creation. |
| 213 |
131285 |
2 |
30 |
Identify a file as suspicious based on how it's packed |
Identifies a packed or encrypted file as suspicious and the packer not used by legitimate software. |
This rule identifies a file as suspicious when it's determined to be packed or encrypted, and there are features in the file that aren't commonly found in legitimate software. |
| 214 |
65750 |
1 |
30 |
Identify a suspicious keylogger |
Identifies a file as suspicious when it has features that aren't used by legitimate software and looks like a keylogger. |
This rule identifies a file as suspicious when it has features that aren't used by legitimate software. The file has suspicious characteristics such as importing APIs which are used to monitor keystrokes, and has missing version information. |
| 217 |
131289 |
2 |
15 |
Identify a suspicious password stealer |
Identifies files that have been incorrectly installed into the user's roaming profile and has suspicious characteristics. |
This rule identifies a file that has been incorrectly installed into the user's roaming profile and has suspicious characteristics. The file imports APIs that are used for monitoring keystrokes, capturing screenshots, or checking for active debuggers. |
| 218 |
65754 |
1 |
30 |
Identify a suspicious file that hides its age |
Identifies files that modify the presented age of the file. The files contain suspicious characteristics and don't look like installed programs. |
This rule identifies files that modify the presented age of the file. The files contain suspicious characteristics such as being packed, missing version information, tagged as a system file, or importing suspicious APIs. They aren't present in a path typically used for installed programs. |
| 219 |
393435 |
6 |
15 |
Identify a suspicious file that hides in a secure location |
Identifies files in secure locations, such as folders reserved for system drivers. These files aren't consistent with other files in that location and have suspicious characteristics. |
This rule identifies files that are in secured locations, such as folders reserved for system drivers. The files don't use the native subsystem, and have suspicious characteristics such as missing or incorrect version information, or a file type that doesn't match the extension. |
| 220 |
196828 |
2 |
30 |
Identify new suspicious files |
Identifies files that are new to the system and contain suspicious characteristics such as modified section names or modified code at the entry point of the binary. |
This rule identifies files that have a creation date in the last 30 days and contain suspicious characteristics. These include modified section names or modified code at the entry point of the binary. |
| 222 |
131294 |
2 |
15 |
Identify a suspicious keylogger hiding as an installed program |
Detects files that import keylogging APIs and hide in locations used by an installed program. They have suspicious characteristics such as a few imports and being new to the system, while not looking like a legitimate application. |
This rule detects files that import keylogging APIs and hide in program file folders or subfolders. The files aren't registered as a service or in add/remove programs. They have registry keys that launch at startup, and suspicious characteristics such as a few imports or Portable Executable (PE) Sections. |
| 234 |
65770 |
1 |
15 |
Identify files that ATD reports as suspicious |
Identifies files that Advanced Threat Defense reports as suspicious. |
This rule identifies files that Advanced Threat Defense reports as suspicious. |
| 235 |
65771 |
1 |
30 |
Identify suspicious files from the Internet that might be malicious based on GTI reputation |
Identifies files that come from the internet which might be malicious based on GTI reputation. |
This rule identifies files that came from an untrusted URL. They're malicious and have suspicious characteristics such as being packed, are less than 15 days old, and appear on less than 10 systems or 1% of the enterprise. |
| 237 |
196845 |
3 |
15 |
Find suspicious files signed with a revoked certificate |
Detects files that have an embedded revoked certificate. They're newly discovered files and are seen on a few systems. |
This rule detects files with an embedded certificate that has been revoked. The files have been in the environment for less than 5 days and are seen on less than 1% of machines. |
| 238 |
655598 |
10 |
-1 |
Identify abuse of common process's spawned from non-standard locations in Observe mode. |
Mitre-T1036: Files may masquerade as legitimate files by hiding in non-standard locations. This rule detects against the suspicious running of common processes if spawned from non-standard locations in Observe mode. |
Tactic: Defense Evasion - Technique: T1036. Identifies the suspicious running of common process's if spawned from non-standard locations. The rule takes a more aggressive approach to rule ID 267 and is by default observe only. It needs to be manually set to enabled in any rule group assignment you want to use it in. |
| 239 |
1179887 |
18 |
-1 |
Identify suspicious command parameter execution |
Mitre-T1059: Identifies the suspicious execution of an application through command-line parameters. |
Tactic: Execution - Technique: T1059. This rule targets suspicious invocations of command and script interpreters. |
| 240 |
65776 |
1 |
30 |
Identify suspicious files with characteristics that have been predominantly seen in ransomware |
Identify suspicious files with characteristics that have been predominantly seen in ransomware and are in uncommonly used locations. |
Identify suspicious files with characteristics that have been predominantly seen in ransomware and are in uncommonly used locations. |
| 243 |
1769715 |
27 |
-1 |
Identify and block suspicious process executions |
Mitre-T1059: blocks suspicious use of command and script interpreters. Similar to rule ID 239 but must be manually enabled. |
Tactic: Execution - Technique: T1059. This rule takes a more aggressive approach than the default on rule ID 239 so it is in observe by default in all rule group assignments. It needs to be manually enabled if you want to use it. |
| 250 |
131322 |
2 |
-1 |
Elevate trust of a file which got scanned multiple times without detection |
Elevate trust of a file based on local age on disk when the file has been scanned multiple times. |
Elevate trust of a file based on local age on disk when the file has been scanned multiple times and has no suspicious characteristics. |
| 251 |
65787 |
1 |
15 |
Identify files that MWG reports as suspicious |
Identifies files that McAfee Web Gateway reports as Known Malicious or Most Likely Malicious and issues a Most Likely Malicious reputation. |
This rule identifies files that McAfee Web Gateway reports as Known Malicious or Most Likely Malicious and issues a Most Likely Malicious reputation. This rule doesn't issue a reputation for files that McAfee Web Gateway determines Might Be Malicious. |
| 252 |
131324 |
2 |
15 |
Identify files that CTD reports as suspicious |
Identifies files that Cloud Threat Detection reports as High or Very High and issues a Most Likely Malicious reputation. |
This rule identifies files that Cloud Threat Detection reports with High or Very High trust score and issues a Most Likely Malicious reputation. This rule doesn't issue a reputation for files that CTD determines with Medium trust score. |
| 253 |
65789 |
1 |
-1 |
Identify malicious or safe files based on Third-party Reputation Provider scores |
Detect or Trust files considering Third-Party Reputation Provider scores. |
Detect or Trust files considering Third-Party Reputation Provider scores connected on the DXL. |
| 255 |
590079 |
9 |
-1 |
Detect potentially obfuscated command-line parameters |
Mitre-T1027: Trigger on command-line arguments that are highly obfuscated. |
Tactic: Defense Evasion - Technique: T1027. This rule is designed to analyze command-line parameters passed to programs to alert on potentially obfuscated strings that could indicate malicious behavior. |
| 256 |
393472 |
6 |
-1 |
Detect use of long -encodedcommand PowerShell |
Mitre-T1059: Command and Scripting Interpreter. Alerts on the usage of -encodedcommand [base64] in PowerShell. |
Tactic: Execution - Technique: T1059. Attempts to look for suspicious usage of the -encodedcommand option in PowerShell. Malware can use this technique to evade static detections of command-line parameters. When this alert is triggered, you should inspect the decoded base64 command to make sure that it's expected behavior. |
| 257 |
393473 |
6 |
15 |
Detect potentially malicious usage of WMI |
Mitre-T1047: Looks for common usage of wmi to either execute code, move laterally or persist. |
Tactic: Execution, Lateral Movement - Technique: T1047. WMI provides a way of discovery, executing code, moving laterally or even persisting in an environment. |
| 258 |
983298 |
15 |
15 |
Detect most likely masqueraded files which can result in suspicious process launches |
Mitre-T1036: Detects files masquerading as legitimate binaries to evade detections. |
Tactic: Defense Evasion - Technique: T1036. This rule is similar to the default on masqueraded file rule ID 259 but includes a different set of files that might trigger false positives. |
| 259 |
590083 |
9 |
15 |
Detect masqueraded files or process launches |
Mitre-T1036: Alerts on if a common system file is renamed or dropped in a non-standard location. |
Tactic: Defense Evasion - Technique: T1036. This rule looks for scenarios where files have been renamed such as script interpreters. |
| 260 |
327940 |
5 |
15 |
Detect AMSI bypass techniques |
Mitre-T1562: Detect the techniques which are used to bypass Antimalware Scan Interface (AMSI). |
Tactic: Defense Evasion - Technique: T1562. This rule is designed to prevent different techniques used to bypass Antimalware Scan Interface (AMSI). |
| 262 |
262406 |
4 |
-1 |
Identify suspicious command parameter execution for Security rule group assignments |
Mitre-T1059 Identifies the suspicious execution of an application through command-line parameters for Security rule group assignments. |
Tactic: Execution - Technique: T1059. This rule identifies suspicious execution of an application through execution parameters for Security rule group assignments. It needs to be manually enabled for Productivity and Balanced rule group assignments. |
| 263 |
917767 |
14 |
-1 |
Detect processes accessing suspicious URLs |
Mitre-T1204. Detect processes accessing suspicious URLs which are used to download malicious content. |
Tactic: Execution - Technique: T1204. This rule is designed to detect processes having suspicious URLs in command parameters used to download malicious payload. |
| 264 |
393480 |
6 |
15 |
Inspect EncodedCommand PowerShell |
Mitre-T1059, T1140: Base64 decode -encodedcommand usage in PowerShell to inspect for suspicious commands. |
Tactics: Execution, Defense Evasion - Techniques: T1059, T1140. This rule decodes base64 encoded commands to check for potential download cradles or other malicious PowerShell usage. |
| 265 |
524553 |
8 |
15 |
Look for executable files with non-standard extensions |
Mitre-T1564: Identify files that are executable (PE) but don't end in a standard extension. |
Tactic: Defense Evasion - Techniques: Mitre-T1564. This rule looks to remove any files identified as a PE file but contains a non-standard extension as identified when running cmd /c assoc. |
| 266 |
786698 |
12 |
30 |
Identify target process launching nonstandard extensions or launched by non-standard actor |
Mitre-T1036, T1059: Attempts to prevent processes trying to launch non-standard extensions or being launched by non-standard actor. |
Tactics: Execution, Defense Evasion - Techniques: T1036, T1059. Detects target process launching non-standard extensions like CScript is launching a txt file. |
| 267 |
262411 |
4 |
-1 |
Protect against abuse of common process's spawned from non-standard locations in security rule group assignments |
Mitre-T1036: Files may masquerade as legitimate files by hiding in non-standard locations. This rule protects against the suspicious running of common process's if spawned from non-standard locations in Security rule group assignments. |
Tactic: Defense Evasion - Technique: T1036. Protect against the suspicious running of common process's if spawned from non-standard locations in Security rule group assignment. It needs to be changed from observe to enabled in Balanced and Productivity rule group assignments. |
| 268 |
262412 |
4 |
-1 |
Protect against abuse of common process's spawned from non-standard locations |
Mitre-T1036: Files may masquerade as legitimate files by hiding in non-standard locations. This rule protects against the suspicious running of common process's if spawned from non-standard locations. |
Tactic: Defense Evasion - Technique: T1036. Protect against the suspicious running of common process's if spawned from non-standard locations. |
| 269 |
196877 |
3 |
15 |
Detect potentially malicious usage of WMI service to achieve persistence |
Mitre-T1047: Looks for common usage of wmi service to execute code and persist. |
Tactic: Execution, Lateral Movement - Technique: T1047. WMI provides a way of discovery, executing code, moving laterally or even persisting in an environment. |
| 270 |
262414 |
4 |
-1 |
Identify and block suspicious command parameters which are manipulated to bypass detection |
Mitre-T1059: blocks suspicious use of command and script interpreters. It blocks patterns which are manipulated to bypass detections. |
Tactic: Execution - Technique: T1059. This rule targets suspicious invocations of command and script interpreters where commands are manipulated to bypass detection. It needs to be manually enabled if you want to use it. |
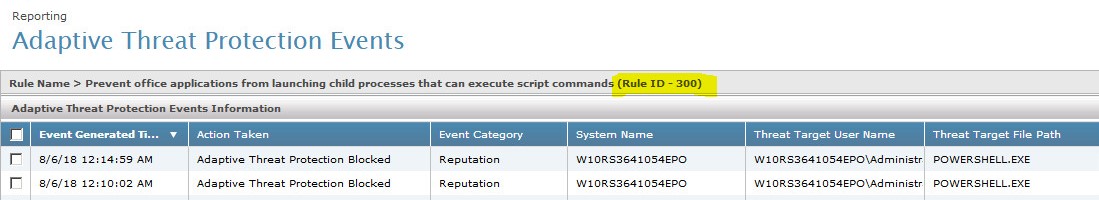
| 300 |
655660 |
10 |
-1 |
Prevent office applications from launching child processes that can execute script commands |
Mitre-T1566: Prevent office applications from launching children processes that can execute scripts like PowerShell and cscript. |
Tactic: Initial Access, Execution, Defense Evasion - Techniques: T1566, T1059. Attempts to prevent office applications from being abused to deliver malicious payloads. |
| 301 |
590125 |
9 |
-1 |
Blocks cmd.exe from being spawned by office applications |
Mitre-T1566: Prevents any office application from launching cmd.exe. |
Tactic: Initial Access, Execution, Defense Evasion - Techniques: T1566, T1059. It's uncommon for cmd.exe to be launched via office documents and can be a sign of malicious behavior. It's recommended you enable this rule if your workflows allow for it. |
| 303 |
327983 |
5 |
-1 |
Identify highly suspicious payloads targeting Browser-related applications |
Identify highly suspicious payloads targeting Browser-related applications like Firefox, Chrome, Edge, and others. |
Identify highly suspicious payloads including unknown binaries targeting Browser applications like Firefox, Chrome, Edge, and others. |
| 304 |
459056 |
7 |
-1 |
Prevent browsers from launching dual use tools such as script editors and cmd |
Prevent browsers from launching dual use tools such as script editors and cmd. |
Prevent browsers from launching dual use tools such as script editors and cmd. |
| 306 |
327986 |
5 |
-1 |
Identify highly suspicious payloads targeting Network related services or applications |
Identifies highly suspicious payloads targeting Network-related services or applications and doesn't allow launch of tools that indicate suspicious behavior. |
Identifies highly suspicious payloads targeting Network-related services or applications and doesn't allow launch of tools that indicate suspicious behavior. |
| 307 |
590131 |
9 |
-1 |
Prevent wmiprvse.exe and netsh.exe from launching script interpreters or other dual use tools |
Prevent wmiprvse.exe and netsh.exe from launching script interpreters or other dual use tools. |
Script interpreters such as PowerShell when invoked via WMI can cause the process wmiprvse.exe to spawn the process making detection harder. Some legitimate processes may use this but it's recommended that you enable this rule if possible to test for false positives. |
| 309 |
590133 |
9 |
-1 |
Block processes trying to launch from office applications. Rule enabled only in high security policies |
Mitre-T1566: Prevent office applications from launching suspect processes. Rule is enabled by default only on the Security rule group assignment. |
Tactic: Initial Access, Execution, Defense Evasion - Techniques: T1566, T1059. Attempts to prevent office applications from being abused to deliver malicious payloads when it's enabled to systems with high security policies. |
| 310 |
131382 |
2 |
-1 |
Prevent email applications from launching child processes that can execute script commands |
Mitre-T1204. Prevent email programs from launching processes that can execute script commands. |
Tactic: Execution - Technique: T1204. Attempts to prevent email applications from being used to further spawn processes that can execute scripts. |
| 311 |
131383 |
2 |
-1 |
Prevent email applications from launching child processes that can execute script commands in Security rule group assignments only |
Mitre-T1204. Prevent email programs from launching processes that can execute script commands only in Security rule group assignments. |
Tactic: Execution - Technique: T1204. Attempts to prevent email applications from being used to further spawn processes that can execute scripts. |
| 312 |
131384 |
2 |
-1 |
Prevent email applications such as Outlook from spawning script editors and dual use tools |
Mitre-T1204. Prevent email applications such as Outlook* from spawning script editors and dual use tools. |
Tactic: Execution - Technique: T1204. This rule helps prevent applications such as Outlook* from spawning potentially abusable tools. Some environments may do this legitimately, so it's recommended that you baseline your environment before enabling. |
| 313 |
262457 |
4 |
-1 |
Prevent several text editors like Notepad and Wordpad from spawning processes that can execute script commands in all rule group assignments |
Mitre-T1204: Prevent text editors from spawning new processes that can further be used to execute scripting commands. |
Tactic: Execution - Technique: T1204. Prevent text editors from being used to spawn processes like cmd or PowerShell. |
| 314 |
262458 |
4 |
-1 |
Prevent several text editors like Notepad and Wordpad from spawning processes that can execute script commands in Security rule group assignment |
Mitre-T1204: Prevent text editors from spawning new processes that can further be used to execute scripting commands in the Security rule group assignment. |
Tactic: Execution - Technique: T1204. Prevent text editors from being used to spawn script interpreters. This rule is only on by default in the Security rule group assignment. It needs to be manually enabled if you're using Balanced or Productivity rule group assignments. |
| 315 |
262459 |
4 |
-1 |
Aggressively blocks processes with unknown reputations from being spawned by text editors |
Mitre-T1204: Aggressively blocks processes with unknown reputations from being spawned by text editors. |
Tactic: Execution - Technique: T1204. Similar to rule ID 313 but takes a more aggressive approach. It's set to observe only by default and needs to be enabled in the rule group assignment. |
| 316 |
262460 |
4 |
-1 |
Prevent PDF readers from launching processes that can execute scripts in all rule group assignments |
Mitre-T1204: Prevent PDF readers from launching processes that can execute scripts. |
Tactic: Execution - Technique: T1204. Prevent PDF readers from launching processes that can execute scripts. |
| 317 |
262461 |
4 |
-1 |
Prevent PDF readers from launching processes that can execute scripts in Security rule group assignments only |
Mitre-T1204: Prevent PDF readers from launching processes that can execute scripts in Security rule group assignments only. |
Tactic: Execution - Technique: T1204. Prevent PDF readers from launching processes that can execute scripts in Security rule group assignments only. |
| 318 |
262462 |
4 |
-1 |
Prevent PDF readers from launching cmd.exe |
Mitre-T1204: Prevent PDF readers from launching cmd.exe |
Tactic: Execution - Technique: T1204. Prevent PDF readers from launching cmd.exe |
| 319 |
196927 |
3 |
-1 |
Prevent cmd.exe from launching other script interpreters such as cscript or PowerShell in all rule group assignments |
Mitre-T1059: Attempts to keep cmd.exe from launching other instances that could indicate a malicious payload. |
Tactic: Execution - Technique: T1059. Block dual use tools from being launched by cmd.exe that are commonly used in attacks. |
| 320 |
131392 |
2 |
-1 |
Prevent cmd.exe from launching other script interpreters such as cscript or PowerShell by default only in Security rule group assignments |
Mitre-T1059: Identify suspicious payloads invoking command shell in the security rule group assignments. |
Tactic: Execution - Technique: T1059. Identify suspicious payloads invoking command shell. This rule is only enabled by default in the Security rule group assignment. It needs to be manually enabled if you're using any other rule group assignment. |
| 321 |
459073 |
7 |
-1 |
Prevent cmd.exe from launching script interpreters |
Mitre-T1059: Attempts to prevent suspicious process chains by keeping cmd from further spawning script interpreting processes. |
Tactic: Execution - Technique: T1059. Attempts to prevent suspicious process chains by keeping cmd from further spawning script interpreting processes. |
| 322 |
459074 |
7 |
-1 |
Prevent mshta from being launched by any process for all rule group assignments |
Mitre-T1218: Prevent mshta from being used as a signed binary to proxy code execution through. |
Tactic: Initial Access, Defense Evasion, Execution - Technique: T1218, T1204. mshta.exe is a common tool used to deliver a payload. This rule prevents it from being used. |
| 323 |
459075 |
7 |
-1 |
Prevent mshta from being launched as a child process |
Mitre-T1218: Prevent mshta from being launched by any process for Security rule group assignments only. |
Tactic: Intial Access, Defense Evasion, Execution - Technique: T1218, T1204. Prevent mshta.exe from being launched by any process. Only on by default in the Security rule group assignment. It needs to be enabled if using Balanced or Productivity rule group assignments. |
| 324 |
655684 |
10 |
-1 |
Prevent mshta from launching suspicious process |
Mitre-T1218: Prevent mshta from launching suspicious application. |
Tactic: Initial Access, Defense Evasion, Execution - Technique: T1218, T1204. This rule takes a more aggressive approach to preventing code executed via mshta.exe and as such is in observe by default in all 3 rule group assignments. It's possible that it could generate false positives and will need to be enabled manually. |
| 325 |
196933 |
3 |
-1 |
Identify suspicious payloads invoking Rundll32 process |
Mitre-T1218: Identify suspicious payloads proxying code execution through the Rundll32 process |
Tactic: Defense Evasion, Execution - Technique: T1218. Identify suspicious payloads proxying code execution through the Rundll32 process. |
| 326 |
328006 |
5 |
-1 |
Identify suspicious payloads invoking Rundll32 in high change systems |
Mitre-T1218: Identify suspicious payloads proxying code execution through the Rundll32 process. |
Tactic: Defense Evasion, Execution - Technique: T1218. Identify suspicious payloads invoking Rundll32. This rule is only on by default in the Security rule group assignment and is set to observe in Balanced and Productivity group assignments. |
| 327 |
328007 |
5 |
-1 |
Identify most probable suspicious payloads invoking Rundll32 process |
Mitre-T1218: Identify most probable suspicious payloads invoking Rundll32 process. |
Tactic: Defense Evasion, Execution - Technique: T1218. This rule is by default in observe only in all 3 rule group assignments. It takes a more aggressive approach to blocking code executed with rundll32 and could generate false positives. It needs to be manually enabled in all rule group assignments. |
| 329 |
393545 |
6 |
-1 |
Identify and block suspicious usage of Scheduled Tasks in high change systems |
Mitre-T1053: Looks for any potentially malicious invoking of schedule tasks and blocks them before being added in high change systems. |
Tactics: Execution, Persistence, Privilege Escalation - Technique: T1053. Looks for any potentially malicious invoking of schedule tasks and blocks them before being added in high change systems. This attempts to cut off malware persistence mechanism. |
| 330 |
262474 |
4 |
-1 |
Identify and block probably suspicious invoking of system process SvcHost and hence preventing it from abuse |
Mitre-T1055: Looks for any potentially malicious invoking of SvcHost system process and blocks it from undesired process injections. |
Tactic: Defense Evasion - Technique: T1055. Looks for any potentially malicious invoking of SvcHost system process and blocks it from undesired process injections from unknown actor processes. |
| 331 |
196939 |
3 |
-1 |
Identify and block probably suspicious invoking of system process SvcHost for Security rule group assignments |
Mitre-T1055. Looks for any potentially malicious invoking of SvcHost system process and blocks it from undesired process injections for security posture. |
Tactic: Defense Evasion - Technique: T1055. Looks for any potentially malicious invoking of SvcHost system process and blocks it from undesired process injections from unknown actor process's for security posture. |
| 332 |
393548 |
6 |
-1 |
Prevent certutil.exe from downloading or decoding files with suspect extensions |
Mitre-T1140: Blocks certutil from downloading remote files or decoding files disguised as something else |
Tactics: Defense Evasion - Techniques: T1140, T1218. CertUtil is a binary that can be abused by attackers to fetch or decode payloads. This rule prevents certutil.exe from fetching payloads or decoding staged files. Certutil also belongs to a group of dual-use tools in the Mitre technique T1218 |
| 333 |
917837 |
14 |
-1 |
Identify probably suspicious process chains |
Mitre-T1574: Identify interesting process chains and block them if behavior is suspicious. |
Tactics: Persistence, Privilege Escalation, Defense Evasion - Technique: T1574. Identify interesting process chains and block them if behavior isn't desirable or suspicious. |
| 334 |
262478 |
4 |
-1 |
Identify registry modifications to suspect locations |
Mitre-T1547: Malware can sometimes maintain persistence by adding or modifying registry keys to instruct a service or binary to launch. |
Tactic: Persistence - Technique: T1547. Identifies and blocks registry modifications to suspicious locations. |
| 335 |
328015 |
5 |
-1 |
Prevent the use of common windows utilities from launching processes in an attempt to bypass UAC |
Mitre-T1548: Attempt to prevent common elevation techniques such as UAC bypasses |
Tactics: Privilege Escalation, Defense Evasion - Technique: T1548. This rule tries to mitigate some common UAC bypass techniques in windows |
| 336 |
196944 |
3 |
-1 |
Detect suspicious payloads targeting Network related services or applications |
Detect suspicious payloads targeting Network related services or applications in security rule group assignments. |
Detect suspicious payloads targeting Network related services or applications via several dual use tools or script interpreters. |
| 337 |
196945 |
3 |
-1 |
Prevent browsers from launching script interpreters or dual use tools in Security rule group assignments |
Detect patterns where browsers trying to launch script editors or dual use tools in security posture. |
Detect patterns where browsers trying to launch script editors or dual use tools and is work as default in security rule group assignments. |
| 338 |
196946 |
3 |
15 |
Detects and Blocks process hollowing attempts for processes that were triggered from an unknown actor |
Mitre-T1055. Detects and Blocks any process hollowing try identified using initial thread state |
Tactics: Defense Evasion, Privilege Escalation - Technique: T1055. Detects and Blocks any process hollowing attempt identified using initial thread state and other relevant process information holders |
| 339 |
131411 |
2 |
-1 |
Prevent .NET utilities to register assemblies from being ran |
Mitre-T1218: Prevent Regsvcs.exe and Regasm.exe from registering and running .NET Assemblies. |
Tactic: Defense Evasion - Technique: T1218. Prevent Regsvcs.exe and Regasm.exe from registering and running .NET Assemblies which can be used to proxy code execution. |
| 340 |
131412 |
2 |
-1 |
Identify and block probably suspicious invocations by SearchProtocolHost and hence preventing it from abuse |
Mitre-T1055: Looks for any potentially malicious invoking of processes by SearchProtocolHost and prevents it from undesired process injections. |
Tactic: Defense Evasion - Technique: T1055. Looks for any potentially malicious invoking of processes by SearchProtocolHost system process and prevents it from undesired process injections. |
| 341 |
196949 |
3 |
-1 |
Identify and block patterns being used in Ransomware attacks in security rule group assignments. |
Looks for any potentially malicious invoking of patterns which are common in Ransomware attacks. It takes more aggressive approach than Rule 342 and works in security rule group assignments. |
Looks for any potentially malicious invoking of patterns which are common in Ransomware attacks and blocks the execution. It takes more aggressive approach than Rule 342 and works in security rule group assignments. |
| 342 |
131414 |
2 |
-1 |
Identify and block patterns being used in Ransomware attacks |
Looks for any potentially malicious invoking of patterns which are common in Ransomware attacks |
Looks for any potentially malicious invoking of patterns which are common in Ransomware attacks and blocks the execution. |
| 343 |
131415 |
2 |
-1 |
Prevent abusable windows binaries from launching cmd.exe as part of a UAC bypass |
Mitre-T1548: Attempt to prevent common elevation techniques such as UAC bypasses |
Tactics: Privilege Escalation, Defense Evasion - Technique: T1548. This rule attempts to mitigate some common UAC bypass techniques in windows |
| 344 |
196952 |
3 |
-1 |
Identify suspicious process chains for Security rule group assignments |
Mitre-T1574: Identify interesting process chains and block them if behavior is suspicious. The rule applies only for Security rule group assignments. |
Tactics: Persistence, Privilege Escalation, Defense Evasion - Technique: T1574. Identify interesting process chains and block them if behavior isn't desirable or suspicious. The rules apply only for Security rule group assignments. |
| 345 |
65881 |
1 |
-1 |
Identify suspicious process execution chains. This is determined by the uncommon occurrence of the process in a specific process chain |
Mitre-T1574: Identify interesting process chains and block them if behavior is suspicious. |
Tactics: Persistence, Privilege Escalation, Defense Evasion - Technique: T1574. Identify interesting process chains and block them if behavior isn't desirable or suspicious. |
| 346 |
196954 |
3 |
-1 |
Prevent certutil.exe from downloading or decoding any file |
Mitre-T1140: Blocks certutil from downloading remote files or decoding files. This rule differs from Rule ID 332 in that it provides more general coverage of certutil abusable parameters. |
Tactics: Defense Evasion - Techniques: T1140, T1218. CertUtil is a binary that can be abused by attackers to fetch or decode payloads. This rule prevents certutil.exe from fetching payloads or decoding staged files. Certutil also belongs to a group of dual-use tools in the Mitre technique T1218. |
| 347 |
393563 |
6 |
-1 |
Prevent actor processes from repeatedly trying to run successive commands |
Mitre-T1059: Command and Scripting. Prevent unknown processes from repeatedly launching commands to stop services or perform other scripted items in a row. |
This is common with recon toolsets and scripts for a process to repeatedly run cmd, PowerShell, wmic, net, etc. to perform quick recon of a system or to stop critical services and processes. |
| 349 |
65885 |
1 |
15 |
Detect potentially malicious usage of BITSAdmin |
Mitre-T1197: Looks for suspicious usage of BITSAdmin tool to download a file in non-standard location or from malicious sites |
Tactic: Defence Evasion, Persistence - Technique: T1197. Looks for suspicious usage of BITSAdmin tool to download a file in non-standard location or from malicious sites |
| 350 |
65886 |
1 |
15 |
Detect suspicious usage of data transfer tools |
Mitre-T1537, T1567: Looks for suspicious usage of tools which can be used to transfer data to an external network |
Tactic: Exfiltration, Technique: T-1537, T-1567. This rule targets to detect data exfiltration by detecting suspicious usage of common data transfer tools. Network traffic related to the tool should be reviewed in case the rule triggers. |
| 500 |
197108 |
3 |
15 |
Block lateral movement from other windows machines in the network |
Mitre-T1570: Lateral Tool Transfer. Blocks use of tools that allow for lateral movement of files to this client. |
Tactic: Lateral Movement - Technique: T1570. This rule blocks lateral movement from Windows Clients. A network data source that monitors traffic may need to be reviewed to make sure this is expected activity. This rule should only be turned on for systems that are in highly restrictive environments as it may generate many false positives. |
| 501 |
131573 |
2 |
15 |
Block lateral movement from other Linux machines in the network |
Mitre-T1570. Blocks all lateral movement to this client from other Linux machines in the network |
Tactic: Lateral Movement - Technique: T1570. This rule blocks lateral movement from Linux Clients. It should only be turned on for systems that are in highly restrictive environments as it may generate many false positives. |
| 502 |
131574 |
2 |
15 |
Detect new service creation |
Mitre-T1543: Prevent new services from being created via sc.exe or powershell.exe. |
Tactic: Persistence, Privilege Escalation - Technique: T1543. New service creation, although common, can be a potential indicator of malicious behavior. New services should be monitored and their underlying execution investigated to make sure it's expected behavior. Services can also be named to masquerade as legitimate services so just the name isn't sufficient to tell legitimate vs malicious services. |
| 503 |
131575 |
2 |
15 |
Detect binaries signed with Suspicious Certs |
Mitre-T1553: Prevent execution of binaries signed with a suspicious cert |
Tactic: Defense Evasion - Technique: T1553-Subvert Trust Controls Code Signing. This rule block execution of binaries signed with untrusted certs. It should only be turned on for systems that are in highly restrictive environments as it may generate many false positives. |
| 504 |
131576 |
2 |
15 |
Prevent use of sdbinst.exe to install application shims |
Mitre-T1546: Prevent use of sdbinst.exe to install application shims. This can be used to patch existing binaries to help establish persistence or escalate privilege. |
Tactic: Privilege Escalation, Persistence - Technique: T1546. Application shimming is a form of event triggered execution and should be carefully monitored for use in your environment. Usage of sdbinst.exe to install an application shim could be an indication of potential malicious behavior. |
| 505 |
131577 |
2 |
15 |
Detect obfuscated cmd.exe command-line parameters |
Mitre-T1027: Detect attempts at obfuscating cmd.exe command-line parameters. Targets tools like Invoke-DOSfuscation |
Tactic: Defense Evasion - Technique: T1027. Attackers can try to bypass command-line detections by obfuscating their payloads. Obfuscated command-line parameters can be an indicator of malicious activity and should be investigated to verify it's expected usage. |
| 506 |
197114 |
3 |
30 |
Detect commands for user discovery |
Mitre-T1033: Detect commands that allow for system owner/user discovery. |
Tactic: Discovery - Technique: T1033. Upon gaining a foothold an attacker may try to use common system administration tools to learn more about the system they have gained access to. This rule can generate false positives due to its generic coverage so it should be enabled with care. |
| 507 |
197115 |
3 |
30 |
Detect commands used to discover more information about a system |
Mitre-T1082: Detect commands commonly used to perform additional recon on a system. |
Tactic: Discovery - Technique: T1082. Upon gaining a foothold an attacker may try to use common system administration tools to further discover details such as hotfixes installed and OS version to better understand the box they have gained initial access to. Caution should be taken when enabling this rule as it can generate false positives due to how generic these commands are. |
| 508 |
197116 |
3 |
30 |
Detect commands used to discover permission information related to users and groups |
Mitre-T1069: Permission groups discovery. |
Tactic: Discovery - Technique: T1069. During the discovery phase of an attack, an adversary may use common tools to enumerate what user and groups have permissions to different assets in the environment. These commands can generate false positives due to how generic they're but can serve as a potential indicator of compromise during the discovery phase of an attack. |
| 509 |
262653 |
4 |
30 |
Detect commands used to discover network-related configurations |
Mitre-T1016, T1049: Detect commands used to discover information related to network configuration and connections information. |
Tactic: Discovery - Technique: T1016, T1049. During the discovery phase of an attack, an adversary may use common tools to enumerate network configuration and network connections. These commands can generate false positives due to how generic they're but can serve as a potential indicator of compromise during the discovery phase of an attack. |
| 510 |
131582 |
2 |
15 |
Detect data encryption attempts for suspicious activities |
Mitre-T1022-T1560: Detect attempts of compression and encryption before exfiltration attempts by suspicious actors. |
Tactic: Collection - Technique: T1560: Detection encryption by third-party softwares or custom methods before exfiltration. The rule is meant for highly restrictive environments and could be prone to false positives. |
| 511 |
197119 |
3 |
30 |
Detect attempts to dump sensitive information via registry or lsass |
Mitre-T1003: Detect commands that can be used to dump sensitive OS information related to credentials. |
Tactic: Credential Access - Technique: T1003. Attackers commonly leverage custom or native tools to export sensitive data such as a memory dump of LSASS.exe, an export of SAM registry hive or make a shadow copy of ntds.dit to facilitate dumping of hashes/credentials. Some software may do this legitimately, so false positives may be generated using this rule. |
| 512 |
197120 |
3 |
30 |
Detect commands that allow for indirect execution outside of cmd and PowerShell |
Mitre-T1202: Detect commands that can execute commands other than cmd or PowerShell. Indirect command execution can be a way for adversaries to evade some detections. |
Tactic: Defense Evasion - Technique: T1202. One way to evade defenses can be to use indirect command execution that may allow for attackers to stay under the radar and bypass detections that may be looking for direct execution via cmd.exe or powershell.exe. Some scripts may legitimately use these commands so false positives may be generated when enabling this rule. |
| 513 |
197121 |
3 |
15 |
Detect commands used for copying files from a remote system |
Mitre-T1105,T1570: Detect commands used to transfer tools or other files from external environment to compromised system. |
Tactic: Command and Control - Technique: T1105, T1570. Block remote copy operations or lateral tool operations from external environment. This rule can generate false positives, hence meant for highly restrictive environments. |
| 514 |
262658 |
4 |
15 |
Detect DLL loads that have potentially been hijacked |
Mitre-T1574: Detect attempts to hijack execution flow by preventing suspicious DLLs from being loaded. |
Tactic: Persistence, Privilege Escalation, Defense Evasion - Technique: T1574. Control flow hijacking can be done a number of ways by abusing the order legitimate binaries attempt to load dependencies. This can allow attackers to use trusted binaries to load an untrusted DLL by taking advantage when the binary isn't explicit of the absolute path where dependencies are expected. |
| 515 |
197123 |
3 |
-1 |
Protect against office apps launching unknown processes from non-standard locations. |
This rule protects against the suspicious use of office apps. It looks for suspicious processes launched by office apps in non-standard locations. |
Office Apps are commonly used to deliver malware, this rule looks for launching of suspicious processes from office apps. This rule can generate false positives so it should be enabled with care. |
| 516 |
131588 |
2 |
15 |
Identify and block processes executing with non-standard command lines |
Attempt to block processes which are executing with command lines normally not seen by the process. |
Tactic: Defense Evasion. This rule targets common windows processes which are executing with non-standard command lines. It needs to be manually enabled if you want to use it. |
| 517 |
131589 |
2 |
15 |
Prevent actor process with unknown reputations from launching processes in common system folders |
This rule looks for actors with an unknown process reputation and prevents it from launching child processes with blank command lines from common system directories. |
This rule targets processes with an unknown process reputation (or lower) launching binaries from common system folders. It also looks for blank command lines as is common in some cobalt strike spawnto uses. |
| 518 |
66054 |
1 |
15 |
Prevent unknown actor processes from launching target processes in common system folders |
This rule is similar to 517 but looks for any unknown actor launching a target with suspicious command-line parameters. |
This rule is similar to 517 but looks for any unknown actor launching a target with suspicious command-line parameters. |
| 519 |
131591 |
2 |
15 |
Detect use of GetSystem command elevate privileges |
Mitre-T1134: Access token manipulation for privilege escalation. This rule looks for named pipe impersonation technique used to get SYSTEM privileges. |
Adversaries can use named pipes to connect to and duplicate the handle to gain SYSTEM privileges. If this rule fires the source and target should be carefully inspected to look for any potential system abuse. |
| 520 |
66056 |
1 |
15 |
Detect abuse of File Permission Modification commands to execute malware |
Mitre-T1222.001: File and Directory Permission Modification. This rule detects suspicious usages of the file system modification commands to execute malware. |
Mitre-T1222.001: File and Directory Permission Modification. This rule detects suspicious usages of the file system modification commands to execute malware. |
| 521 |
131593 |
2 |
15 |
Detect attempts to hijack a service whose path is unquoted |
Mitre-T1574.009: Hijack Execution Flow via path interception. |
Tactics: Persistence, Privilege Escalation, Defense Evasion. Service paths that aren't properly quoted may be hijackable by placing a binary in a folder that is searched before the intended service |
| 522 |
66058 |
1 |
15 |
Detect attempts to hijack execution flow via search order of the PATH environment variable |
Mitre-T1574.007: Hijack Execution Flow via PATH environment variable interception. |
Tactics: Persistence, Privilege Escalation, Defense Evasion. The order of the paths in the PATH environment variable can be susceptible to execution hijacking. |
| 523 |
66059 |
1 |
15 |
Detect services or scheduled tasks launched from a suspect location |
Mitre-T1036.004: Masquerade Task or Service |
Tactics: Persistence, Privilege Escalation, Defense Evasion. Malware may use a scheduled task or service for persistence or to escalate privileges. To evade detection, they may masquerade the name of the service or task to look legitimate. If this rule triggers scheduled tasks and services should be inspected for legitimacy. |
| 524 |
66060 |
1 |
15 |
Prevent any execution of cmd.exe from mshta.exe |
This rule is designed to prevent execution of cmd.exe from mshta.exe |
Prevent execution of cmd.exe spawning from mshta.exe process. |