Apache has released
Log4j 2.16.0 to address this vulnerability (Updated: 12/14). We recommend applying this update to impacted systems and reviewing relevant
Log4j configurations in your environment to identify potential workflows that might be subject to this vulnerability. For third-party applications, contact the application vendors on steps to do so.
There have been a multitude of methods observed where attackers can use
Log4Shell. There's a broad scope and scale of this vulnerability, and the only definitive way to be inoculated from risk is to both apply vendor updates, and review application configurations. These actions make sure that the vulnerability is mitigated as per Apache's recommendations. As with all major zero-days, the best security approach is to assume that you've already been scanned, are being targeted, and applying remediation or mitigation steps with absolute priority. We're working tirelessly to provide coverage for this threat and ensure that security administrators are enabled in their investigations when evaluating their environments.
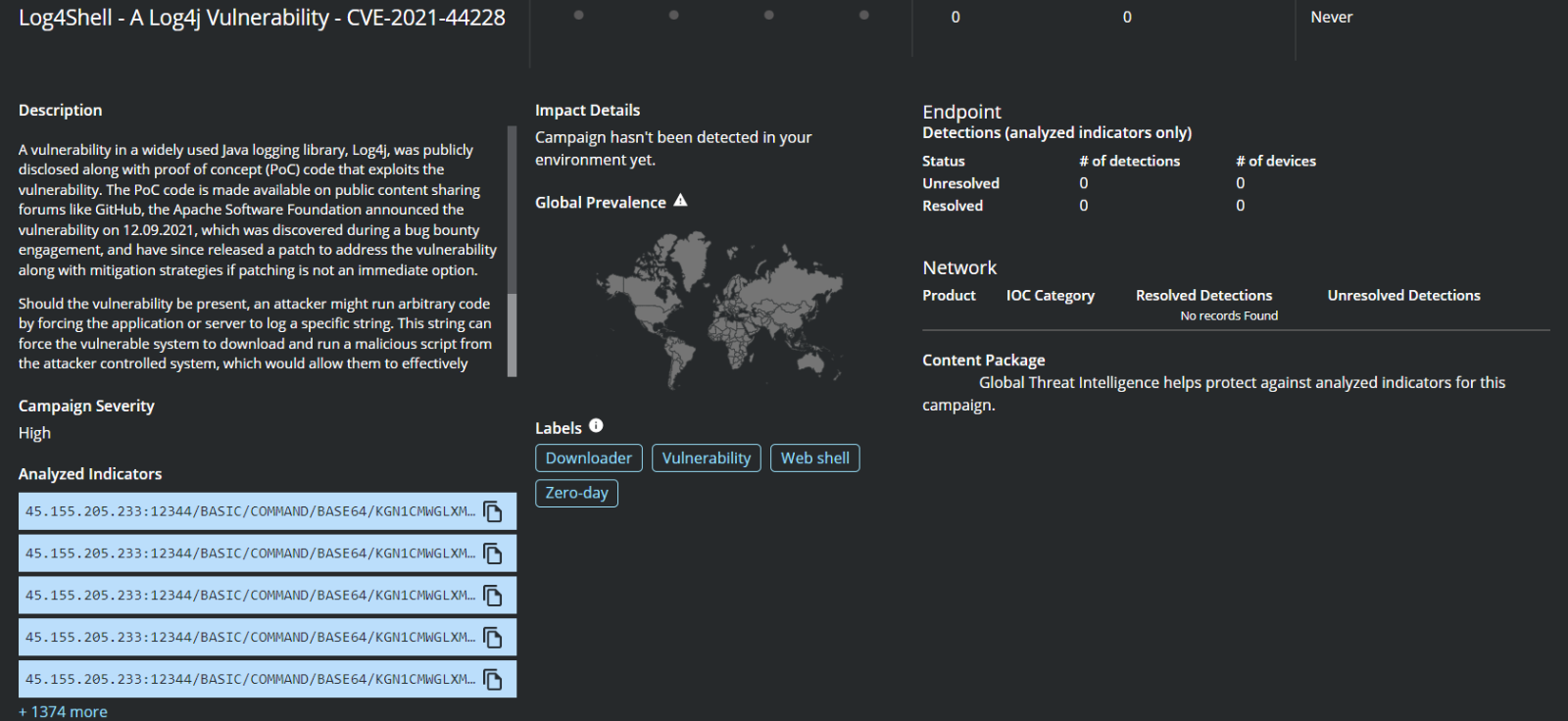
Are Trellix products impacted by this vulnerability?
We're reviewing all products within our portfolio to evaluate their potential impact and the risk to customers. On December 13, 2021, we published a formal Security Bulletin to provide customers guidance on products that are impacted with this vulnerability. The aim was to outline products that don't include the
Log4j component, or are otherwise not at risk.
For information about whether a product in your environment is affected, workaround, and mitigation steps, and other product-related information, see
SB10377 - REGISTERED - Security Bulletin - Product status for "Log4Shell" (CVE-2021-44228, CVE-2021-4104, CVE-2021-45046, CVE-2021-45105 and CVE-2021-44832).
NOTE: The referenced content is available only to logged in ServicePortal users. To view the content, click the link and log in when prompted.
Updates will continue to be provided, as they become available.
To receive email notification when this article is updated, click Subscribe on the right side of the page. You must be logged on to subscribe.
How can Trellix product solutions help?
It's always advised, and a best practice, to make sure that software and operating systems are kept up to date on available updates and security updates as they're released. We also recommend evaluating and implementing general countermeasures against entry-level threats where suited in your environment. For more information, see
KB91836 - Countermeasures for entry vector threats. Many of these methods, while not addressing the vulnerability themselves, can severely inhibit actors' post-exploitation capabilities and provide visibility for security administrators to respond appropriately.
We're evaluating product coverage across our portfolio of security solutions. This article will be updated as possible coverage opportunities and countermeasures are identified.
Product capabilities are currently available for the following components:
Detection and Response:
Endpoint Security (ENS) ExtraDAT, Expert Rule Process Memory Scan Trigger:
We've developed a solution to enable administrators in identifying and responding to active attempts to exploit CVE-2021-44228 in their environment. This solution is a two-fold approach, leveraging the ability of ENS Expert Rules in versions
10.7.0 2020 November Update (Release Notes) and later, to react to triggers by calling an On-Demand Memory Scan of the target process. This approach requires two prerequisites be applied to the endpoint:
- You must apply the ExtraDAT provided in the "Attachment" section of this article to provide content for the On-Demand Memory Scans to detect on JNDI related strings in process memory.
IMPORTANT: On December 21, a new ExtraDAT was added to this article in the archive EXTRA2.zip. For more information, see the "Tuning the Expert Rule for your Environment" section below.
- You must implement the Expert Rule in your ENS Exploit Prevention policy, and set to REPORT only. The Expert Rule doesn't provide sufficient protection alone to be valuable in a block capacity, and doing so risks potential conflict with legitimate processes in your environment. Setting the rule to REPORT only makes sure that it triggers the On-Demand Memory scans when the rule is violated, without risking unintended blocks.
NOTE:
- It's important that this configuration is tested thoroughly to ensure rule integrity, and to prevent any potential conflict. Once testing confirms that the rule is viable for your environment, customers are encouraged to apply this mechanism to Windows Server Platforms where Java-based applications are potentially exposed to network connectivity from the internet. For example, Apache Tomcat, Elastic Search servers, etc. Doing so decreases the likelihood of false positives and the additional tuning measures that those results might require. Applying this content to general user Windows Workstations isn't recommended.
- We're reviewing options for making this content available for MVISION customers as well. Subscribe to this article to be informed when updates are made.
- This configuration results in two events being generated when potentially malicious behavior is detected. The first detection reflects the Exploit Prevention rule trigger. The second detection reflects the On-Demand Memory Scan detecting potentially malicious behavior. If only the first event is received, the memory scan doesn't identify any malicious JNDI-related strings in the process memory. If the second event is received, indicating that the On-Demand Memory Scan detects a JNDI-related string in process memory, administrators must take immediate action on the system identified.
- The following image depicts examples of the two different possible detection threat types. Note the threat type Trojan, with Threat Source Process 'on-demand scan.' This event type is the second-stage event, and indicates that administrators must take immediate action.

Implementing the ExtraDAT and Exploit Prevention Rule:
- Check in the ExtraDAT file in ePO through the 'Check-in Package' function of the Master Repository page. Or, for testing or non-managed endpoints, apply the ExtraDAT through the ENS console.
For more information, see KB67602 - How to check in and deploy an Extra.DAT in ePolicy Orchestrator and KB93673 - Apply Extra.DAT locally using the Endpoint Security Client.
Once checked in, the ExtraDAT reflects the following name in the Master Repository, and within client tasks ExtraDAT (JNDI.Log4J-Exploit.a;JNDI.Log4J.Exploit.b;JNDI.Log4J.Exploit.c)
NOTE: We offer a tool to merge ExtraDATs in the Support Portal if you receive another extra driver that must be applied to your environment.
- Make sure that the Client Update Tasks to endpoints includes the ExtraDAT package type, and that these updates are applied to systems. Once the ExtraDAT is deployed to systems expected to receive the Expert Rule, continue with modifying your policies on step 3.
- To configure the Expert Rule, navigate to your Endpoint Security, Exploit Prevention policy. Add an Expert Rule configured with the following settings:
| Rule Name |
JNDI Log4J Exploit |
| Severity |
High |
| Action |
Report |
| Rule Type |
Processes |
- Apply the following rule contents to the rule:
Rule {
Reaction SCAN ACTOR_PROCESS ScanAction REPORT
Process {
Include OBJECT_NAME {
-v "java.exe"
-v "javaw.exe"
-v "tomcat*.exe"
}
Include AggregateMatch -xtype "dll1" {
Include DLL_LOADED -name "java" { -v 0x1 }
}
Include AggregateMatch -xtype "dll2" {
Include DLL_LOADED -name "jvm" { -v 0x1 }
}
}
Target {
Match PROCESS {
Include OBJECT_NAME { -v "cmd.exe" }
Include OBJECT_NAME { -v "powershell.exe" }
Include OBJECT_NAME { -v "powershell_ise.exe" }
Include OBJECT_NAME { -v "wscript.exe" }
Include OBJECT_NAME { -v "cscript.exe" }
Include OBJECT_NAME { -v "rundll32.exe" }
Exclude PROCESS_CMD_LINE { -v "* chcp 1252 *" }
}
}
}
-
Save the modified rule and policy. Apply it to the endpoints that have received the appropriate
ExtraDAT content.
Tuning the Expert Rule for your Environment:
The Expert Rule is designed to trigger a targeted On-Demand Scan (ODS). The rule doesn't indicate that a threat is present on the system(s). You can safely ignore
Log4J Exploit Prevention events not followed by an ODS detection event. Large numbers of these Exploit Prevention events might be generated by normal operations, and don't indicate a false positive as the rule criteria are met to trigger the ODS task. To manage the events, see the "Schedule purging the Threat Event Log" section of the
ePO 5.10 Product Guide.
The benefit of this approach is to invoke a targeted ODS memory scan based on the Expert Rule trigger. So, further exclusions aren't needed and might reduce the ODS efficacy of the rule. But, you can finely tune the Expert Rule for your environment. Tuning the rule makes sure that ENS only scans process memory when it's needed. Make sure that the rule is applied to systems with potentially vulnerable applications through targeted policy assignment and ePO system grouping. This action can prevent unnecessary coverage, and you can tune the rule further to ignore natural application behavior.
For the Technical Support statement for custom rules with ENS, see
KB94889 - Support statement for custom rules with Endpoint Security. If you alter the rule as provided in this article, make sure that you
validate and enforce the Expert Rule on a client system before applying the policy in ePO. For more information, see the "Validate and enforce an Expert Rule on a client system" section of the
ENS 10.7 Product Guide.
There are three main sections of the rule that you must focus on.
ACTOR Processes: These processes refer to all processes that the Expert Rule is expected to monitor. This section includes application executables that leverage Java, or might be known to contain
Log4j. This section allows the Expert Rule to monitor their activity for potential calls to the Target section.
TARGET section: This section includes any binaries that might be considered suspicious if started from the ACTOR process. The Expert Rule compares the details with common fileless attack vectors such as '
wscript.exe' and '
powershell.exe'. If the ACTOR process invokes a binary listed in the TARGET section, the Expert Rule resolves to the REACTION section.
You can exclude legitimate process activity by the command-line parameters used at process execution by adding a line like the following to the
Target section of the rule.
Examples:
Exclude PROCESS_CMD_LINE { -v "* chcp 1252 *" }
Exclude PROCESS_CMD_LINE { -v "* ping 127.0.0.1*" }
This allows processes that would otherwise trigger the rule to be excluded based on the specified command-line parameters in use. The same action without the specified parameter would still trigger the rule. The command-line parameter will vary and should be unique enough so that it doesn't exclude unintended events. ePO administrators can see the
Log4J Exploit Prevention Threat Events in their environments to determine what parameters might be needed.
NOTE: Owing to the nature of the rule, exclusions by process alone aren't beneficial as only predefined processes are included.
REACTION section: This section refers to the first line inside the rule,
Reaction SCAN ACTOR_PROCESS ScanAction REPORT. This line tells Exploit Prevention that when the ACTOR process has invoked a TARGET, to begin a process memory scan of the affected processes. Any reactions other than REPORT are applied to the ACTOR process, which might be your vulnerable application running. That means that if we detect TOMCAT being exploited, the cleaning might be applied to
TOMCATxx.EXE itself. It's recommended to leave the rule in REPORT only and isolate the system using other means (such as EDR quarantine) if a detection occurs. But, multiple options are available for reactions. It's recommended that you test before implementing.
NOTE: The
ExtraDAT provided in this article has been updated to provide enhanced functionality on December 21, 2021. Customers who applied the
ExtraDAT before December 21 must redeploy the new enhanced version (
EXTRA2.zip). The changes in this
ExtraDAT allow CLEAN actions to be directed at the TARGET process without impacting the parent ACTOR process. For example, if
Java.exe launches
cmd.exe due to an exploit, the detection stops the
cmd.exe process without stopping
java.exe. This allows administrators to react and investigate the system while limiting potential disruption in production applications.
- CLEAN_PROCESS - Attempt to clean the process. The detection is logged to the ODS Activity Log.
- DELETE_PROCESS - Attempt to delete the process. The detection is logged to the ODS Activity Log.
- CLEAN_DELETE_PROCESS - First, attempt to clean the process; if unsuccessful, attempt to delete the process. The detection is logged to the ODS Activity Log.
- REPORT - Take no action on the detected process. The detection is logged to the ODS Activity Log and a detection event is sent to ePO.
- REPORT_CLEAN_PROCESS - Attempt to clean the process. The detection is logged to the ODS Activity Log and a detection event is sent to ePO.
- REPORT_DELETE_PROCESS - Attempt to delete the process. The detection is logged to the ODS Activity Log and a detection event is sent to ePO
- REPORT_CLEAN_DELETE_PROCESS - First, attempt to clean the process; if unsuccessful; attempt to delete the process. The detection is logged to the ODS Activity Log and a detection event is sent to ePO.
ENS, VirusScan Enterprise (VSE), Secure Web Gateway (SWG):
On December 12, 2021, we released
V3 AMCore content 4648,
MEDDAT 4818.0000, and
V2 DAT 10196. Generic detections are provided under the title
Exploit-CVE-2021-44228.C. These detections identify the use of potentially malicious
jndi:ldaps, jndi:ldap,
jndi:rmi, and
jndi:dns strings. Detections are represented as a "Potentially Unwanted Program," and it's recommended that you review policies to make sure that scanners honor Unwanted Program detections.
Other detections continue to be added, and it's recommended that customers continue to update endpoint and gateway content following our daily release cadence.
Enabling Unwanted Program detections:
ENS: On-Access Scan Policy, Process Settings (Make sure that the setting is adjusted for all risk profiles where applicable.)
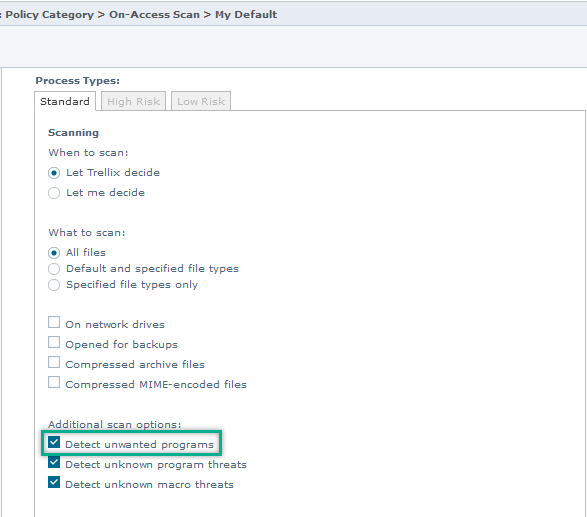
VSE: On-Access Scan Policy
Detections are also available for samples related to in-the-wild campaigns exploiting this vulnerability. This list might not be all inclusive, and samples are being continually evaluated for detection.
| Hash |
Detection Name |
| 0579a8907f34236b754b07331685d79e |
Linux/Black-T.a |
| 07b7746b922cf7d7fa821123a226ed36 |
Linux/Coinminer.bl |
| 648effa354b3cbaad87b45f48d59c616 |
LINUX/Kinsing.a |
| ccef46c7edf9131ccffc47bd69eb743b |
LINUX/Downloader.bb |
| 09c5608ec058a3f1d995a4340b5d204b |
Exploit-CVE-2021-44228.d |
| 671182fa65c043c5643aca73a2827553 |
Exploit-CVE-2021-44228.d |
| 0af9f06338c94bc026787a85d06af5ac |
Exploit-CVE-2021-44228.d |
| 2b4303e6a9346781bd70f32290f97d4f |
Exploit-CVE-2021-44228.d |
| 751249af62035965a26ab90ff9c652f2 |
Exploit-CVE-2021-44228.d |
| eab89d2f9511d79a7ea10477320b93bd |
Exploit-CVE-2021-44228.d |
| e29b1df3acaa1dd701fa123e362ab52d |
Exploit-CVE-2021-44228.d |
| b8519db943405027127c8a8b919fde9e0c5f9c9f |
BAT/Agent.bp |
| f43a96d6970e8252894d6a53c6858bf2ab75149f |
BAT/Agent.bp |
| 716167b08e01e9c5919b8e8458e59e8e9ad68826 |
BAT/Agent.bs |
| c927738922b87802cc75697dd99dd8c7d8cfdf1e |
Linux/Black-T.a |
| 8611063eefa5cc2bbec29870fb56779192eed454 |
Linux/Black-T.a |
| bf2df8f2813ef4e2cf61ea193e091b808aa854c7 |
Linux/Coinminer.bl |
| ffe3dda2486083d0b26f1c64ac300923088e01df |
Linux/Coinminer.bl |
| 38c56b5e1489092b80c9908f04379e5a16876f01 |
LINUX/Downloader.bb |
| 8654b19a3fd4e3e571cc84c0c3990669c04e3558 |
Linux/Gates |
| 0194637f1e83c2efc8bcda8d20c446805698c7bc |
LINUX/Kinsing.a |
| 296273fd9965bf41d8d3970c766158c7f24fc618 |
LINUX/Tsunami.u |
| 61586a0c47e3ae120bb53d73e47515da4deaefbb |
LINUX/Tsunami.u |
| 43c1c41fdb133c3f9c25edcdff16e229ac31f42b |
LINUX/Tsunami.u |
| 335d6b7d76d2918ef133fe9d4735ae201616323b |
LINUX/Tsunami.u |
| e3eb1e98ca477918154b9ed7bcc2b7fe757c1020 |
LINUX/Tsunami.u |
| fd91820560d2e0aa7079d7c7756e343e66f47056 |
LINUX/Tsunami.v |
| 82d984fcbf4f8bc8ffbad29e3f3cc4cfac70d8d4 |
LINUX/Tsunami.v |
| b21aa1107ecc79f4ad29f68a026a02e2abc952ef |
LINUX/Tsunami.v |
| 0c876245dfdeb17c0ad472b0356cd5658b384f6a |
LINUX/Tsunami.v |
| edcacb6b71a0a66736f8b3dd55aaae371e4171b8 |
LINUX/Tsunami.v |
| e121d1050bf62a94adfde406325e70a7878b3ed8 |
LINUX/Tsunami.v |
| 3c7a4da4190ceac25f28719794e2b9e6d62105c1 |
LINUX/Tsunami.v |
| 2e75071855d7f1c78eed2e6e971e763451c6298c |
LINUX/Tsunami.v |
| 237315820fe77880e892d5c30b2f5fde7e5f6d64 |
LINUX/Tsunami.v |
| 7c1808a5296ece6400e4ec558b9ef0d82e0f23b0 |
LINUX/Tsunami.v |
| 5008672d6f47a444c743455346e0b04eef257b30 |
LINUX/Tsunami.v |
| 74402152ac0f0c9dfed6f76975080ce1d0d4584d |
Linux-coinminer.d |
| 18791de615208b29809e840771e11ac8c3b5ed7b |
PS/Reverseshell.a |
| 0d4404b132e6e297974eca391f176a047ad7ed73 |
PUP-XOK-HR |
| cef612c5c042cceddff8b6b8bc573bb0af46a208 |
GenericRXNV-AC!F5271F6B20FD |
| 9147d834f4cb7047a6e6ab96565868c6fede373e |
RDN/Generic Downloader.x |
| 95d9a068529dd2ea4bb4bef644f5c4f5 |
RDN/Generic.dx |
| 18cc66e29a7bc435a316d9c292c45cc6 |
W64/CoinMiner |
| 0BB39BA78FC976EDB9C26DE1CECD60EB |
Linux/Tsunami!0BB39BA78FC9 |
| 0F7C2DD019AFCC092FD421EE52431AFF |
JAVA/Agent.f |
| 1348A00488A5B3097681B6463321D84C |
Linux/Log4Shell |
| 163E03B99C8CB2C71319A737932E9551 |
Coinminer.cp |
| 1780D9AAF4C048AD99FA93B60777E3F9 |
Coinminer.cp |
| 194DB367FBB403A78D63818C3168A355 |
W64/CoinMiner |
| 1CF9B0571DECFF5303EE9FE3C98BB1F1 |
Coinminer.cp |
| 1E051111C4CF327775DC3BAB4DF4BF85 |
BAT/Downloader.ax |
| 1FE52C0B0139660B2335DD7B7C12EA05 |
LINUX/Coinminer.cl |
| 20DF80B56B1B6FFC8CA49F8AD3AB7B81 |
Linux/Mirai!20DF80B56B1B |
| 39FC2CEE0A2BEA3EE9A065F6955FFD43 |
Java/Agent!39FC2CEE0A2B |
| 51E052EB6032D11B3093FECB901870EA |
Linux/Mirai!51E052EB6032 |
| 7B8CE524AE078A76A69548AEBB95CB7E |
Main.class JAVA/Agent.i |
| 844864C45816B10356B730F450BD7037 |
Linux/Mirai!844864C45816 |
| 963B4F516B86C9D8B30BEFE714CEDB22 |
Linux/Downloader.bv |
| AB80C03C460BD3D6A631FD0CEDDDEF49 |
Linux/Mirai!AB80C03C460B |
| C6E8E6BB0295437FB790B1151A1B107E |
Linux/Mirai!C6E8E6BB0295 |
| C717C47941C150F867CE6A62ED0D2D35 |
W64/CoinMiner |
| D766BD832973A991C5894A3521C9815E |
Linux/Mirai!D766BD832973 |
| F14019C55E7CE19D93838A4B2F6AEC12 |
BAT/Downloader.ax |
| F5271F6B20FDA39C213FD9579AD7E1FB |
Linux/Tsunami!F5271F6B20FD |
| F65F547869CA35A8E2902C4DEC0DD97F |
LINUX/Coinminer.cb |
| F8ED43117DFB995F4B9D88F566394BA4 |
CVE-2021-44228!F8ED43117DFB |
Customers must make sure that all solutions receive the most current content as they're released, which occurs on a daily cadence. Doing so makes sure that as coverage is added, it's made readily available to provide protection.
SWG:
SWG Classic 10.2 and later can identify and block malicious JNDI lookup patterns that trigger the
Log4Shell vulnerability via the rule set "Search for Log4Shell" (available in the "Attachment" section of this article). This works for requests, and the benefits are as follows:
- When using SWG as a reverse proxy, systems behind it are protected against Log4Shell exploits in HTTP headers and body (GAM detects exploit patterns in a POST request out of the box with recent DAT updates).
- When using SWG as a forward proxy, attacks originating from your own network with a POST request via the proxy are blocked.
To apply/import the rule set, perform the steps below:
- Place the rule set 2021-12-13_10-50_Search for Log4Shell.xml (available in the "Attachment" section of this article) on the desktop.
- Click Add and then Top Level Rule Set.
- Click Import rule set from Rule Set Library.
- Click Import from file.
- Select the file.
- Resolve all conflicts.
- Click OK.
- Move the rule setup to an appropriate place in the policy, ideally where SSL scanning is enabled.
- Click Save Changes.
UCE and SWG can also protect against download of Java class files. The simplest approach is to block the media type "
application/java-vm" (found in the media type category "Executables") completely. If legitimate class file download needs to be allowed, granting access by IP address or domain is recommended. See the file
2021-12-20_15-16_Block Java Class Files.xml (available in the "Attachment" section of this article) for SWG. To import the rule set, follow similar steps as above. In UCE, you can create a similar rule set easily via the policy UI.
Trellix Intrusion Prevention System (Trellix IPS) User-Defined Signature:
- Protection against these vulnerabilities is included in all current signatures.
Hunting, Vulnerability Assessment, and Investigation:
- MVISION Endpoint Detection and Response (EDR), Trellix Active Response (TAR):
You can use the 'Real-Time Search' and 'Historical Search' functionality to proactively hunt for vulnerable systems or exploit activity within your environment.
We maintain a GitHub repository of useful 'Real-Time Search' queries that administrators might find to aid them in their investigation. For more information, see RTS Queries GitHub.
Built-in collectors can enable searching for the following:
Self-assessment of reported vulnerable versions of Log4j by hash can be accomplished with a foundational query. For example:
HostInfo os, hostname, platform
AND Files sha256, full_name
WHERE HostInfo platform equals "Linux"
AND Files sha256 equals "bf4f41403280c1b115650d470f9b260a5c9042c04d9bcc2a6ca504a66379b2d6"
OR Files sha256 equals "bf4f41403280c1b115650d470f9b260a5c9042c04d9bcc2a6ca504a66379b2d6"
OR Files sha256 equals "58e9f72081efff9bdaabd82e3b3efe5b1b9f1666cefe28f429ad7176a6d770ae"
OR Files sha256 equals "ed285ad5ac6a8cf13461d6c2874fdcd3bf67002844831f66e21c2d0adda43fa4"
OR Files sha256 equals "dbf88c623cc2ad99d82fa4c575fb105e2083465a47b84d64e2e1a63e183c274e"
OR Files sha256 equals "a38ddff1e797adb39a08876932bc2538d771ff7db23885fb883fec526aff4fc8"
OR Files sha256 equals "7d86841489afd1097576a649094ae1efb79b3147cd162ba019861dfad4e9573b"
OR Files sha256 equals "4bfb0d5022dc499908da4597f3e19f9f64d3cc98ce756a2249c72179d3d75c47"
OR Files sha256 equals "473f15c04122dad810c919b2f3484d46560fd2dd4573f6695d387195816b02a6"
OR Files sha256 equals "b3fae4f84d4303cdbad4696554b4e8d2381ad3faf6e0c3c8d2ce60a4388caa02"
OR Files sha256 equals "dcde6033b205433d6e9855c93740f798951fa3a3f252035a768d9f356fde806d"
OR Files sha256 equals "85338f694c844c8b66d8a1b981bcf38627f95579209b2662182a009d849e1a4c"
OR Files sha256 equals "db3906edad6009d1886ec1e2a198249b6d99820a3575f8ec80c6ce57f08d521a"
OR Files sha256 equals "ec411a34fee49692f196e4dc0a905b25d0667825904862fdba153df5e53183e0"
OR Files sha256 equals "a00a54e3fb8cb83fab38f8714f240ecc13ab9c492584aa571aec5fc71b48732d"
OR Files sha256 equals "c584d1000591efa391386264e0d43ec35f4dbb146cad9390f73358d9c84ee78d"
OR Files sha256 equals "8bdb662843c1f4b120fb4c25a5636008085900cdf9947b1dadb9b672ea6134dc"
OR Files sha256 equals "c830cde8f929c35dad42cbdb6b28447df69ceffe99937bf420d32424df4d076a"
OR Files sha256 equals "6ae3b0cb657e051f97835a6432c2b0f50a651b36b6d4af395bbe9060bb4ef4b2"
OR Files sha256 equals "535e19bf14d8c76ec00a7e8490287ca2e2597cae2de5b8f1f65eb81ef1c2a4c6"
OR Files sha256 equals "42de36e61d454afff5e50e6930961c85b55d681e23931efd248fd9b9b9297239"
OR Files sha256 equals "4f53e4d52efcccdc446017426c15001bb0fe444c7a6cdc9966f8741cf210d997"
OR Files sha256 equals "df00277045338ceaa6f70a7b8eee178710b3ba51eac28c1142ec802157492de6"
OR Files sha256 equals "28433734bd9e3121e0a0b78238d5131837b9dbe26f1a930bc872bad44e68e44e"
OR Files sha256 equals "cf65f0d33640f2cd0a0b06dd86a5c6353938ccb25f4ffd14116b4884181e0392"
OR Files sha256 equals "5bb84e110d5f18cee47021a024d358227612dd6dac7b97fa781f85c6ad3ccee4"
OR Files sha256 equals "ccf02bb919e1a44b13b366ea1b203f98772650475f2a06e9fac4b3c957a7c3fa"
OR Files sha256 equals "815a73e20e90a413662eefe8594414684df3d5723edcd76070e1a5aee864616e"
OR Files sha256 equals "10ef331115cbbd18b5be3f3761e046523f9c95c103484082b18e67a7c36e570c"
OR Files sha256 equals "dc815be299f81c180aa8d2924f1b015f2c46686e866bc410e72de75f7cd41aae"
OR Files sha256 equals "9275f5d57709e2204900d3dae2727f5932f85d3813ad31c9d351def03dd3d03d"
OR Files sha256 equals "f35ccc9978797a895e5bee58fa8c3b7ad6d5ee55386e9e532f141ee8ed2e937d"
OR Files sha256 equals "5256517e6237b888c65c8691f29219b6658d800c23e81d5167c4a8bbd2a0daa3"
OR Files sha256 equals "d4485176aea67cc85f5ccc45bb66166f8bfc715ae4a695f0d870a1f8d848cc3d"
OR Files sha256 equals "3fcc4c1f2f806acfc395144c98b8ba2a80fe1bf5e3ad3397588bbd2610a37100"
OR Files sha256 equals "057a48fe378586b6913d29b4b10162b4b5045277f1be66b7a01fb7e30bd05ef3"
OR Files sha256 equals "5dbd6bb2381bf54563ea15bc9fbb6d7094eaf7184e6975c50f8996f77bfc3f2c"
OR Files sha256 equals "c39b0ea14e7766440c59e5ae5f48adee038d9b1c7a1375b376e966ca12c22cd3"
OR Files sha256 equals "6f38a25482d82cd118c4255f25b9d78d96821d22bab498cdce9cda7a563ca992"
OR Files sha256 equals "54962835992e303928aa909730ce3a50e311068c0960c708e82ab76701db5e6b"
OR Files sha256 equals "e5e9b0f8d72f4e7b9022b7a83c673334d7967981191d2d98f9c57dc97b4caae1"
OR Files sha256 equals "68d793940c28ddff6670be703690dfdf9e77315970c42c4af40ca7261a8570fa"
OR Files sha256 equals "9da0f5ca7c8eab693d090ae759275b9db4ca5acdbcfe4a63d3871e0b17367463"
OR Files sha256 equals "006fc6623fbb961084243cfc327c885f3c57f2eba8ee05fbc4e93e5358778c85"
File hashes for
Log4j 2.x versions sourced from
GitHub.
Identify systems with vulnerable versions of
Log4j installed by file name. For example: Files and HostInfo hostname where Files name contains
log4j.
File names might differ between versions, or if
Log4j is delivered via a vendor solution.
.png)
.png)
Identify outbound communication attempts to known callout domains.
Identify Indicators of Compromise associated with exploit payloads.
NOTE: On Linux,
.JAR files are excluded from File Hashing by default. To provide accurate visibility in your environment, remove
.JAR from your EDR Policies
File Hashing,
Ignore Extensions on Linux settings. This change doesn't require that file systems be rehashed completely.

- SIEM
We've released Exploit Content Pack version 4.1.0, which is now available for download from the rules server. This content pack contains a new alarm titled "Exploit - Possible Log4Shell Exploit." This alarm looks at the URL and User_Agent fields for the specific jndi string to denote a possible exploit attempt.
For more information about SIEM Exploit Content pack 4.1.0, see KB85403 - REGISTERED - SIEM Content Packs for Exploit.
NOTE: The referenced content is available only to logged in ServicePortal users. To view the content, click the link and log in when prompted.
Threat Intelligence:
Product capabilities determined to be out of scope:
- ENS Exploit Prevention. For details about leveraging Exploit Prevention Expert Rule functionality with On-Demand memory scans, see the above "Detection and Response" section.









.png)
.png)