Threat Intelligence Exchange recommended workflow
Last Modified: 2023-05-19 12:20:19 Etc/GMT
Affected Products
Languages:
This article is available in the following languages:
 Loading...
Loading...
Trellix CEO, Bryan Palma, explains the critical need for security that’s always learning.

As per Gartner, "XDR is an emerging technology that can offer improved threat prevention, detection and response."

Trellix announced the establishment of the Trellix Advanced Research Center to advance global threat intelligence.

Trellix Advanced Research Center analyzes threat data on ransomware, nation-states, sectors, vectors, LotL, MITRE ATT&CK techniques, and emails.
As of May 14, 2024, Knowledge Base (KB) articles will only be published and updated in our new Trellix Thrive Knowledge space.
Log in to the Thrive Portal using your OKTA credentials and start searching the new space. Legacy KB IDs are indexed and you will be able to find them easily just by typing the legacy KB ID.
Threat Intelligence Exchange recommended workflow
Technical Articles ID:
KB86307
Last Modified: 2023-05-19 12:20:19 Etc/GMT Environment
Threat Intelligence Exchange (TIE) Server - all supported versions For supported environments, see KB83368 - Supported platforms for Threat Intelligence Exchange Server. SummaryTo make effective use of TIE capabilities, follow a scalable workflow. The ideal process periodically cycles a multi-stage funnel that prioritizes detailed analysis.
Activities:
TIE enables the following activities within ePolicy Orchestrator (ePO):
The workflow cycle looks as follows: 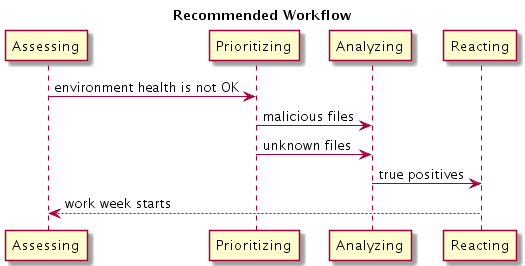 Scaling: To scale as the number of indicators grows, do the following:
To add new base images to the managed environment with minimal disruptions, do the following:
Affected ProductsLanguages:This article is available in the following languages: |
|
