Application and Change Control blocks script configured as an updater
Last Modified: 2024-01-31 11:07:06 Etc/GMT
Affected Products
Languages:
This article is available in the following languages:
 Loading...
Loading...
Trellix CEO, Bryan Palma, explains the critical need for security that’s always learning.

As per Gartner, "XDR is an emerging technology that can offer improved threat prevention, detection and response."

Trellix announced the establishment of the Trellix Advanced Research Center to advance global threat intelligence.

Trellix Advanced Research Center analyzes threat data on ransomware, nation-states, sectors, vectors, LotL, MITRE ATT&CK techniques, and emails.
As of May 14, 2024, Knowledge Base (KB) articles will only be published and updated in our new Trellix Thrive Knowledge space.
Log in to the Thrive Portal using your OKTA credentials and start searching the new space. Legacy KB IDs are indexed and you will be able to find them easily just by typing the legacy KB ID.
Application and Change Control blocks script configured as an updater
Technical Articles ID:
KB92291
Last Modified: 2024-01-31 11:07:06 Etc/GMT Environment
Application and Change Control (ACC) 8.x
Summary
Script As Updater (SAU) is needed if a script file has to make changes to the solidified system. It's required to modify the solidified file and execute unsolidified files. Any script that's configured as an updater, doesn't get the updater privilege in some cases. Example and explanation: Script files aren't executed like other executables or binaries. They're run through the interpreter process (binary) that understands the commands or scripting in the file. For example, For example, suppose there are three bat files, echo “11111” test2.bat: echo “22222” test3.bat: copy /y test1.bat test2.bat Solidify all files and make If you look at the logs generated closely for both the cases: When the script is run in the same process In the example, the script is run directly from the command prompt as 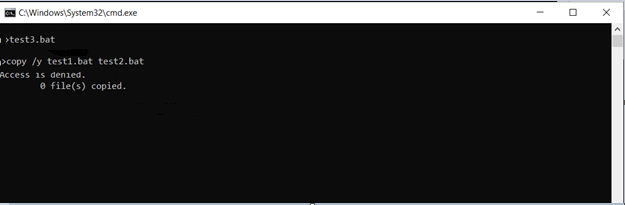 The following event is seen in the Solidcore logs: When the script is run from the same process ACC doesn't allow the process to modify the solidified file When the script is run in a new process In the example, double-click or execute .png) The following event is seen in the Solidcore logs ( When the script is run a new process ACC allows the process to modify the solidified file only in that specific process lifecycle. Double-click and " Affected ProductsLanguages:This article is available in the following languages: |
|
