DLP Endpoint process crashes on HSP-enabled endpoints when integrated with Titus or AIP
Last Modified: 2023-10-18 03:57:37 Etc/GMT
 Loading...
Loading...
Trellix CEO, Bryan Palma, explains the critical need for security that’s always learning.

As per Gartner, "XDR is an emerging technology that can offer improved threat prevention, detection and response."

Trellix announced the establishment of the Trellix Advanced Research Center to advance global threat intelligence.

Trellix Advanced Research Center analyzes threat data on ransomware, nation-states, sectors, vectors, LotL, MITRE ATT&CK techniques, and emails.
After December 1, 2024, please log in to the Thrive Portal for support, knowledge articles, tools, and downloads. For information about using the Thrive Portal, view the Trellix Thrive Portal User Guide.
DLP Endpoint process crashes on HSP-enabled endpoints when integrated with Titus or AIP
Technical Articles ID:
KB96826
Last Modified: 2023-10-18 03:57:37 Etc/GMT Environment
Data Loss Prevention (DLP) Endpoint 11.10.x Windows 10 and 11 Titus SDK Microsoft Information Protection SDK For supported environments, see KB68147 - Supported platforms for Data Loss Prevention Endpoint. Problem
The DLP Endpoint for Windows process crashes on Hardware-enforced Stack Protection (HSP)-enabled endpoints when integrated with Titus or AIP. On Control-flow Enforcement Technology (CET) / HSP, the supported hardware Cause
The crash isn't due to the DLP Endpoint for Windows quality issues. Trellix DLP binaries have been complied with CET to support HSP. The Titus SDK (3.1.14.13) and AIP are compiled with .NET 4.7.2, which doesn't support CET. Hence, they fail the CET security checks, resulting in the error. The shadow stack protections terminate the DLP process. This is due to third-party DLLs being loaded into the Trellix DLP Endpoint process ( Solution
Titus SDK and MIP SDK are required to support CET/HSP for proper integration.
WorkaroundThe HSP must be disabled in the following processes.
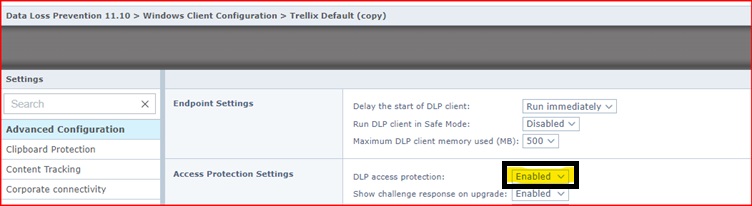
C:\Program Files\McAfee\DLP\Agent\fcagte.exe To disable HSP, first, you must disable DLP access protection by performing the following steps: NOTE: Disabling DLP access protection isn't recommended. Enable the setting immediately after disabling Exploit protection for DLP process.
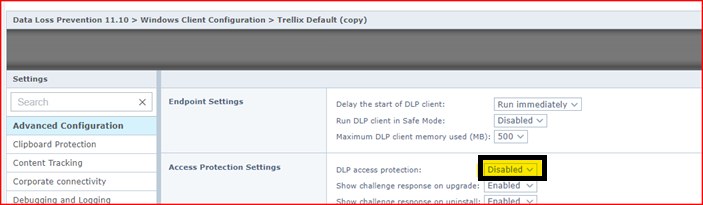 HSP can be disabled using three methods:
For details about these methods, see Import, export, and deploy exploit protection configurations.
Following are the steps to disable the DLP process
This mitigation can be controlled like other exploit protections, including toggling the enforcement using the Windows Defender UI.
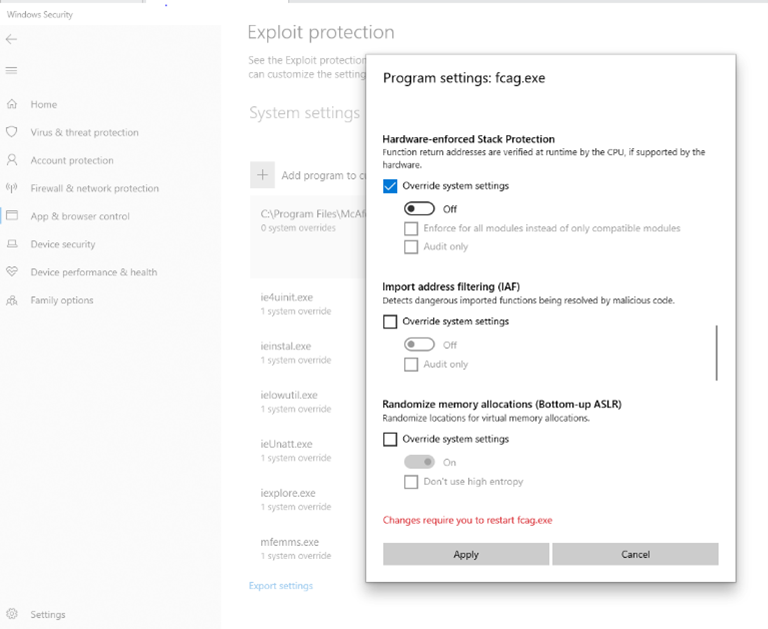 NOTE: Follow the same steps mentioned above for
Run the following command through
An XML file can be exported from "Export Settings" in the Exploit protection page and imported into the GPO.
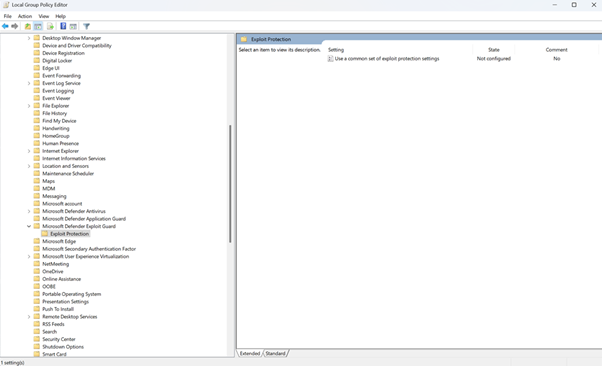
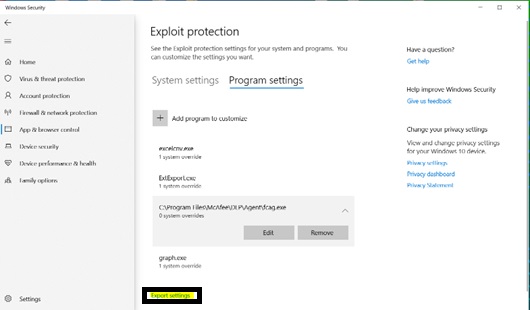 The XML file contains the following entries: Use Group Policy to distribute the configuration:
Following are the steps to enable the DLP Access Protection:
 Related Information
For more information on HSP, see the following documentation:
Affected Products |
|
