We're aware of variants of
Emotet detected in corporate environments. Threat Name:
Emotet-FEJ
Read the official Threat Advisory in
KB91854 - Threat Advisory: Emotet.
Minimum DATs for coverage:
- VirusScan Enterprise (VSE) 8736 or higher *
- Endpoint Security (ENS) 3187 or higher *
* Trellix-defined content protection against known variants.
As a best practice, configure repository update tasks with a minimal refresh interval. This configuration makes sure that new content is applied when we release it.
IMPORTANT: Before you implement the following recommendations, you must thoroughly test the rules to check their integrity. You must also make sure that no legitimate application (developed in-house or otherwise) is deemed malicious and prevented from functioning in your production environment. You can set the rules suggested below in "report-only" mode for testing purposes to verify that they cause no conflict in your environment. When you determine that these rules don't block any activity from legitimate applications, set the rules to block and apply these settings to all relevant systems.
VSE and ENS Access Protection Proactive Measures
For reference purposes, see the following KB articles to configure Access Protection Rules in VSE and ENS:
Use VSE Access Protection rules:
Rule1:
Rule: Common Maximum Protection - Prevent creation of new executable files in the Windows folder
Rule Category: Downloader/Payload/Isolation
Rule Aggression: Aggressive
Rule2:
Rule Type: File/Folder Blocking Rule
Process to include: winword.exe
File or folder name to block: cmd.exe
File actions to prevent: Files being executed
Rule Category: Downloader
Rule Aggression: Mildly Aggressive
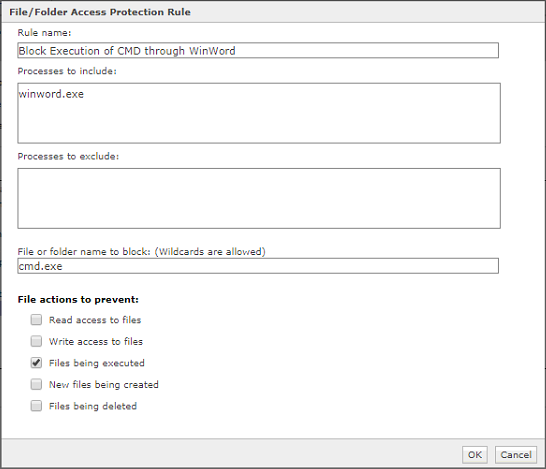
Rule3:
Rule Type: File/Folder Blocking Rule
Process to include: winword.exe
File or folder name to block: powershell.exe
File actions to prevent: Files being executed
Rule Category: Downloader
Rule Aggression: Mildly Aggressive
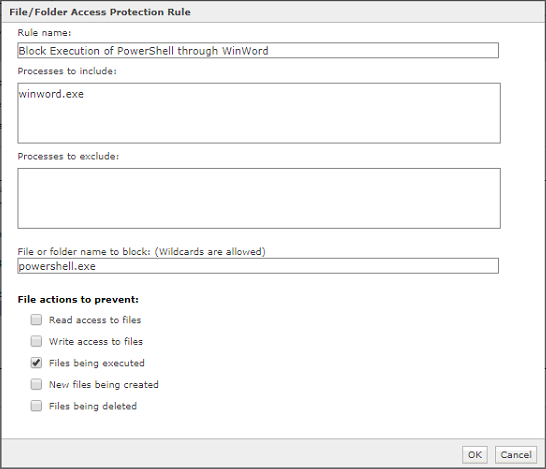
Rule4:
Rule Type: File/Folder Blocking Rule
Process to include: *
File or folder name to block: C:\*.exe
File actions to prevent: New files being created
Rule Category: Isolation
Rule Aggression: Aggressive
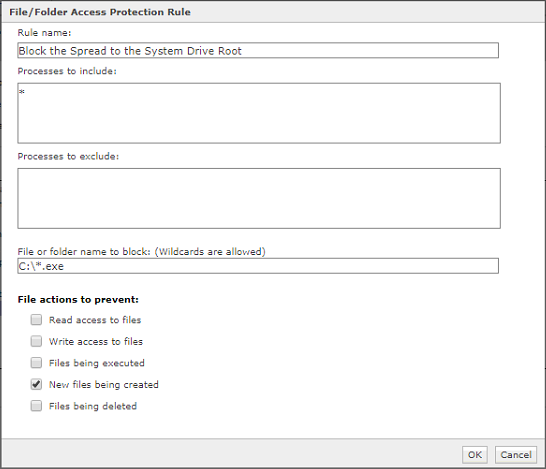
Use ENS Access Protection rules:
Rule1:
Rule Name: Creating new executable files in the Windows folder
Rule Category: Downloader/Payload/Isolation
Rule Aggression: Aggressive
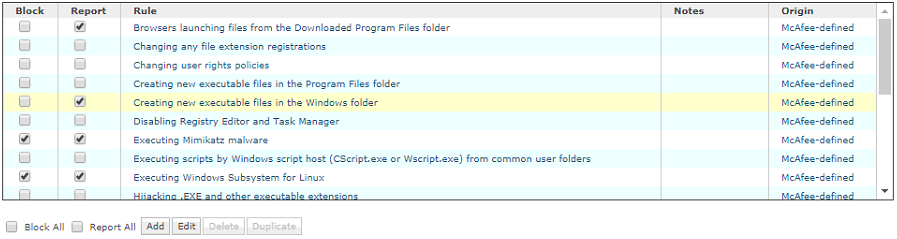
Rule2:
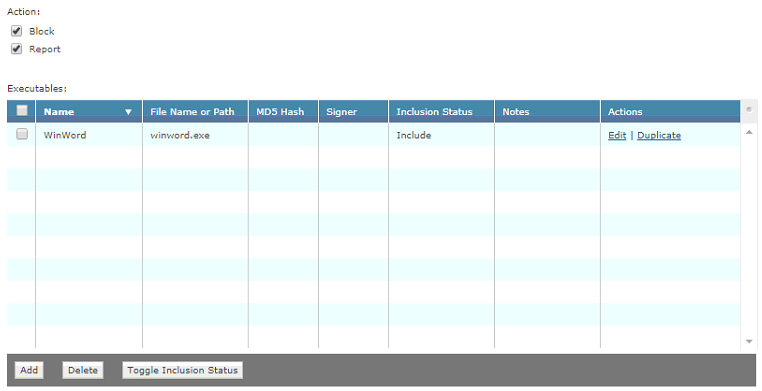
Executable1:
Inclusion: Include
File Name or Path: winword.exe
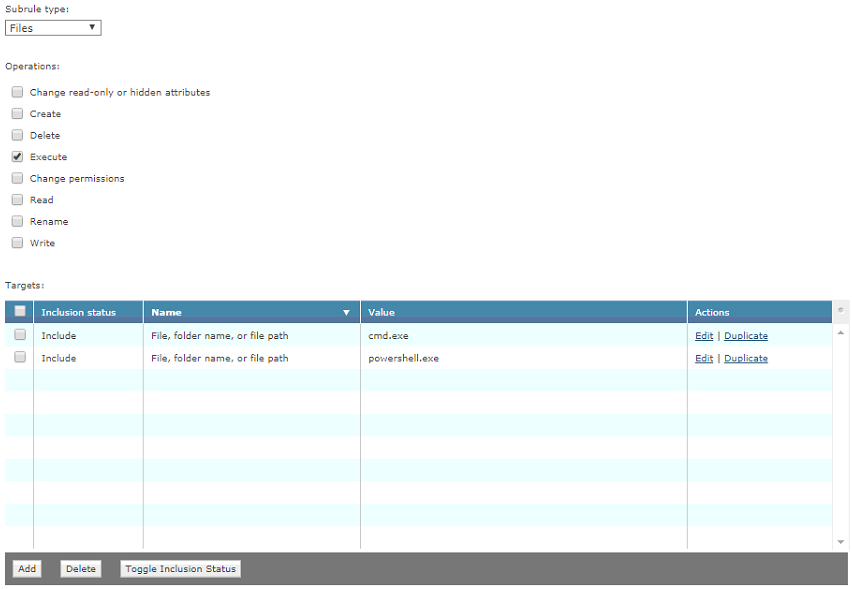
SubRule1:
SubRule Type: Files
Operations: Execute
Target1:
Inclusion: Include File, folder name, or file path 1:
cmd.exe
File, folder name, or file path 2: powershell.exe
Rule Category: Downloader
Rule Aggression: Mildly Aggressive
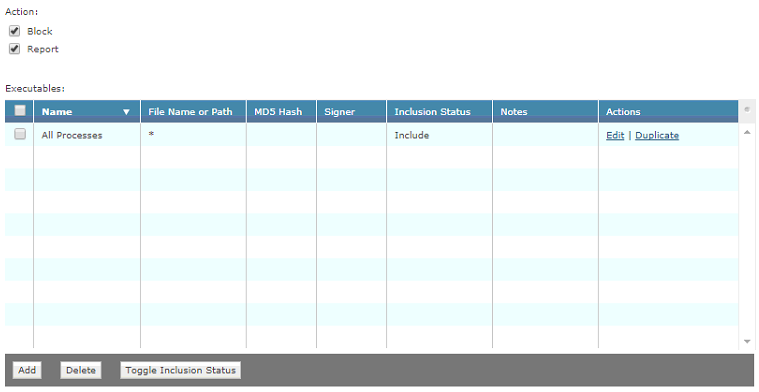
Rule3:
Executable1:
Inclusion: Include
File Name or Path: *
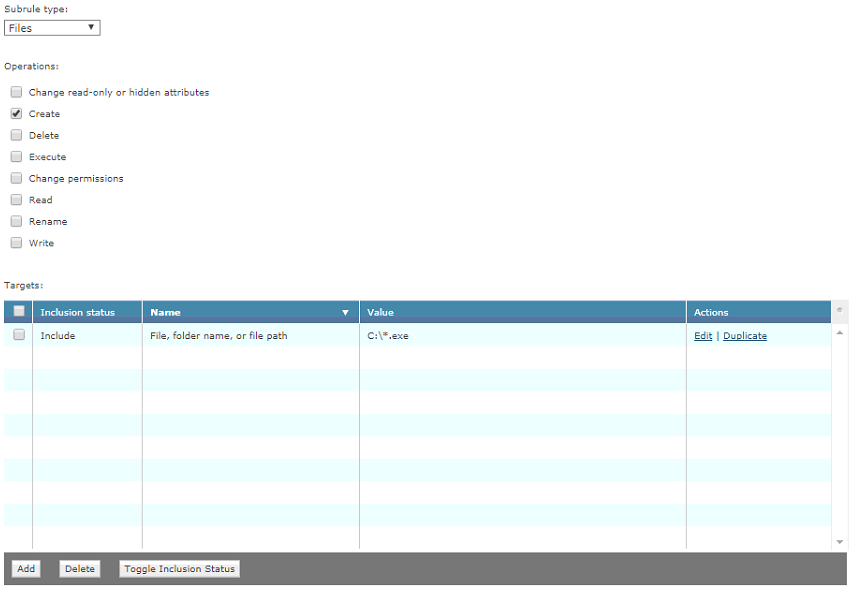
SubRule1:
SubRule Type: Files
Operations: Create
Target1:
Inclusion: Include
File, folder name, or file path: C:\*.exe
Rule Category: Isolation
Rule Aggression: Aggressive
Use ENS Exploit Prevention rules:
Rule1:
Rule ID: 6087
Rule Name: PowerShell Command Restriction – EncodedCommand
Rule Category: Downloader
Rule Aggression: Aggressive
Host Intrusion Prevention (Host IPS) Proactive Measures
This section provides additional information about observed Host IPS rules triggered by known
Emotet variants.
Use of Host IPS rules:
Rule1:
Rule ID: 6010
Rule Name: Generic Application Hooking Protection
Rule Category: Downloader/Payload
Rule Aggression: Aggressive
Rule2:
Rule ID: 6011
Rule Name: Generic Application Invocation Protection
Rule Category: Downloader/Payload
Rule Aggression: Aggressive
Rule3:
Rule ID: 6087
Rule Name: PowerShell Command Restriction – EncodedCommand
Rule Category: Downloader
Rule Aggression: Aggressive
Rule4:
Rule ID: 1148
Rule Name: CMD Tool Access by a Network Aware Application
Rule Category: Downloader
Rule Aggression: Aggressive
ENS with Adaptive Threat Protection (ATP) – Real Protect and Dynamic Application Containment (DAC)
ENS with ATP Real Protect, with DAC, provides next-generation protection against unknown exploits.
ENS with ATP provides full protection against all known variants of
Emotet. We recommend the following ATP configuration for detection of unknown
Emotet variants:
- Configure the following setting in the ATP - Options Policy:
Rule Assignment = Security (default setting is Balanced)
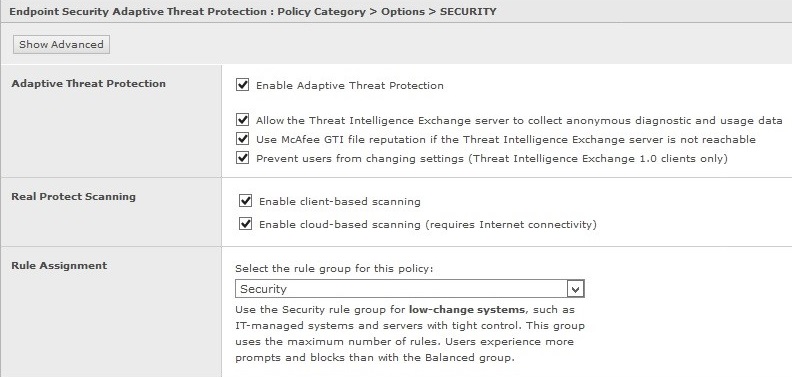
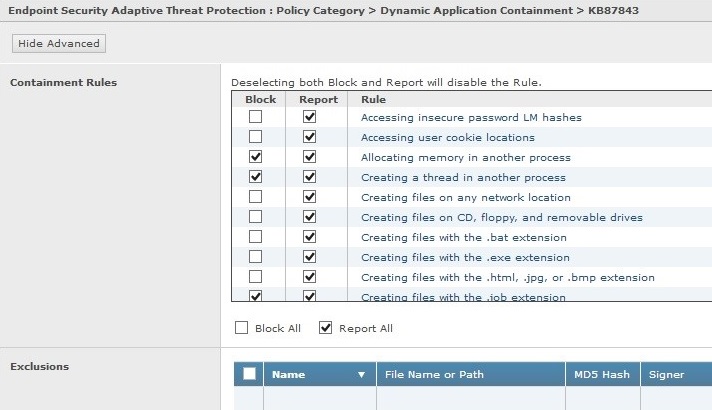
- Configure the following rules in the ATP – DAC policy:
DAC – Containment Rules
See KB87843 - List of and best practices for Endpoint Security Dynamic Application Containment rules. Set the recommended DAC rules to Block as prescribed.
ENS DAC rules triggered by Emotet variants
This section provides additional information about observed DAC rules triggered by known
Emotet variants. More rule enablement might not be needed to effectively contain related processes not detected by other layers of the ENS security stack.
See
KB87843 - List of and best practices for Endpoint Security Dynamic Application Containment rules. Set the recommended DAC rules to Block as prescribed:
Rule1:
Rule Name: Modifying the hidden attribute bit
Rule Category: Payload
Rule Aggression: Cautious
Rule2:
Rule Name: Executing any child process
Rule Category: Payload Rule
Aggression: Mildly Aggressive
Rule3:
Rule Name: Modifying the Services registry location
Rule Category: Payload
Rule Aggression: Mildly Aggressive
Rule4:
Rule Name: Modifying portable executable files
Rule Category: Payload
Rule Aggression: Mildly Aggressive
Rule5:
Rule Name: Creating files with the .exe extension
Rule Category: Payload
Rule Aggression: Aggressive


















